Doctor Web’s annual virus activity review for 2018
[% DEFAULT FILE_REVIEW = ''; NAME_SOME_ARRAY_IN_MACROSNAME = [ { box => "Overview" }, { box => "Most notable events" }, { box => "Malware landscape" }, { box => "Encryption ransomware" }, { box => "Linux" }, { box => "Dangerous websites" }, { box => "Network fraud" }, { box => "Mobile devices" }, { box => "Prospects and trends" } ] %] [% BLOCK global.tpl_blueprint.content %]
December 28, 2018
The year 2018 saw the spread of Trojans for coverting cryptocurrency mining. The malicious software targeted not only Microsoft Windows users, but also various Linux device owners. Encoders that encrypt files on infected computers and demand a ransom for decryption are not losing their momentum either. In February and April, Doctor Web experts detected two new additions to this family. One of them was unable to repair the files even after payment, despite the claims of virus writers.
In late March 2018, we investigated
Throughout the year, cybercriminals had been luring their victims to fake websites and sending them bulk emails. At the beginning of the year, the attackers were sending emails on behalf of the Mail.Ru Group, trying to get ahold of their users’ logins and passwords; while in spring, they switched to sending fake cash reward offers. In summer, spammers continued pestering domain administrators, posing as representatives of the RU-CENTER hosting provider and demanding payments to renew the registration of domain names owned by potential victims.
In 2018, users of Google Android mobile devices did not escape the attention of virus writers. Back in January, information security experts detected infected games that were downloaded from Google Play more than 4,500,000 times. A little later, we discovered Android mining software that could infect 8% of various smart devices, such as TVs, streaming boxes, routers, and other IoT devices.
Throughout the year, malware analysts had been warning users about the spread of banking Trojans for Android with the widest range of functions. Analysts also detected several fake apps posing as popular Android applications used for phishing. Some mobile Trojans signed their victims up to chargeable services, others earned money through invisible advertising, and we also discovered Trojans that downloaded other malware onto the infected device.
Principal trends of the year
- The spread of Trojan miners, designed to covertly mine cryptocurrencies using hardware of infected computers
- New malicious programs for Linux and IoT
- More malware for devices running Google Android
Most notable events of 2018
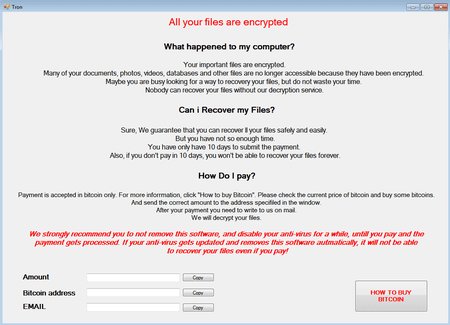
In February 2018, a new Trojan encoder was detected and added to the Dr.Web virus database as
Another encoder, known as
Unfortunately, the code of this Trojan contained more than one error, so even its authors eventually found it impossible to decrypt the corrupted files. This once again emphasizes the importance of timely backup of all important files.
In late March, Doctor Web analysts investigated the spyware
A month and a half later, our experts managed to find the author of these Trojans. The malware and its modifications were stealing stored passwords and cookies from Chrome browsers, information from Telegram, FileZilla FTP client, images, and office documents according to a predetermined list. One of the Trojan’s modifications was actively advertised on various Telegram channels. Logins and passwords to cloud storages, where the archives with the stolen files were uploaded to, were embedded in the Trojans, so that Doctor Web’s virus analysts identified both the author of malware and all their customers. This investigation was described in detail in the corresponding article on our website.
Another investigation made public in late May, centered around the author of spyware that stole personal data from Steam game platform users. The attacker used several money extraction methods at once including, fraudulent roulettes (auctions, where users can sell different game items) won by bots but created by the fraudster, as well as malware rentals. To spread the Trojans, the cybercriminal used social engineering methods and fake websites.
Operating principles of spyware
In summer, Doctor Web analysts warned users about the new miner
In September, Doctor Web specialists discovered the banking malware
When users attempted to open the online banking page of various Brazilian financial organizations, the Trojan replaced it with a fake login and password entry form. In some cases, it prompted the user to specify the verification code from the text message they received from the bank. This information was then transmitted to attackers. Our virus analysts have identified over 340 unique instances of
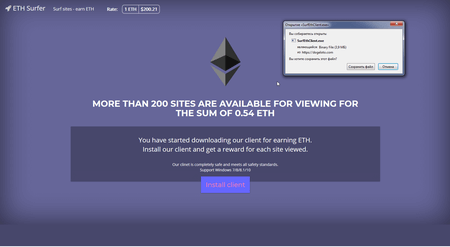
Another investigation ended in mid-October. We looked into the activities of a cybercriminal in the cryptocurrency market. The attacker used a whole range of malware, such as Eredel, AZORult, Kpot, Kratos, N0F1L3, ACRUX, Predator The Thief, Arkei, Pony, and many more.To achieve their goals, they created several phishing websites to replicate real Internet resources. Among them were a fake cryptocurrency exchange, a pool of devices for Dogecoin mining, allegedly leased at competitive prices, and a partner program offering a reward for viewing Internet websites.
Another project is an online lottery with the prize consisting of a certain amount of Dogecoin cryptocurrency. Lotteries were designed in so that it was impossible for a third-party participant to win; only the organizer could make money. Other initiatives included, traditional phishing schemes and an affiliate program offering Dogecoins for browsing web pages with ads. When a user tried to download a client for that purpose, they would actually download a Trojan from the cybercriminal's website. Read more on these types of fraud in our article.
In November, the malware
According to Doctor Web analyst information, some 1,400 users have been affected by this Trojan by now, with the first cases occurring in 2013. See more information on this incident in the newsletter on our website.
Virus situation
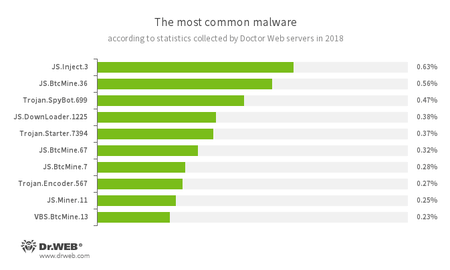
According to Doctor Web statistics servers, 2018 saw many malicious JavaScript scripts embed third-party content into web pages and mine cryptocurrencies, as well as Trojan spyware and malicious loaders.
- JS.Inject
- A family of malicious JavaScripts that injects a malicious script into the HTML code of webpages.
JS.BtcMine - A family of JavaScript scenarios designed to covertly mine cryptocurrencies.
Trojan.SpyBot.699 - A multi-module banking Trojan. It allows cybercriminals to download and launch various applications on an infected device and their commands to be executed. The Trojan is intended to steal money from bank accounts.
JS.DownLoader - A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer.
- Trojan.Starter.7394
- A Trojan whose main purpose is to launch an executable file with a specific set of malicious functions in an infected system.
- Trojan.Encoder.567
- An encryption ransomware Trojan that encrypts files and demands a ransom to decrypt the compromised data.
- JS.Miner
- A family of JavaScript scenarios designed to covertly mine cryptocurrencies.
- VBS.BtcMine
- A family of VBS scripts designed to covertly mine cryptocurrencies.
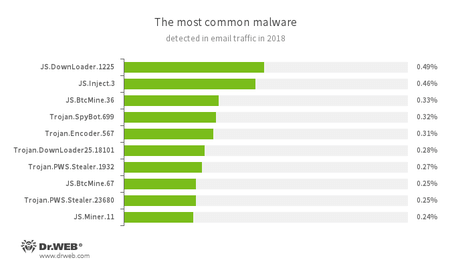
A similar picture is observed in the analysis of mail traffic; but overall, spyware Trojans are much more common in email attachments:
JS.DownLoader - A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer.
- JS.Inject
- A family of malicious JavaScripts that injects a malicious script into the HTML code of webpages.
JS.BtcMine - A family of JavaScript scenarios designed to covertly mine cryptocurrencies.
Trojan.SpyBot.699 - A multi-module banking Trojan. It allows cybercriminals to download and launch various applications on an infected device and their commands to be executed. The Trojan is intended to steal money from bank accounts.
- Trojan.Encoder.567
- A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom to decrypt compromised data.
Trojan.DownLoader - A family of malicious programs designed to download other malware to the compromised computer.
Trojan.PWS.Stealer - A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
- JS.Miner
- A family of JavaScript scenarios designed to covertly mine cryptocurrencies.
Encryption Trojans
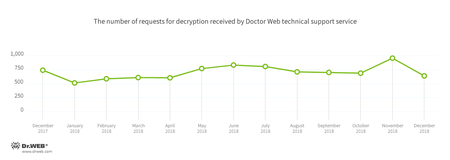
Compared with the previous year, the number of user calls to Doctor Web technical support due to encryptions by Trojan encoders dropped in 2018. We saw a slight rise in the number of victims from May to August. The fewest calls were recorded in January, while November saw the greatest.
According to statistics, the
The most common ransomware programs in 2018:
Trojan.Encoder.858 — 19,83% requests;Trojan.Encoder.11464 — 9,64% requests;Trojan.Encoder.567 — 5,08% requests;Trojan.Encoder.11539 — 4,79% requests;- Trojan.Encoder.25574 — 4,46% requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Linux malware
In 2018, malicious programs for Linux most often manifested themselves as miners. The first such attacks on Linux servers were detected by Doctor Web virus analysts in early May 2018. Cybercriminals connected to a server via SSH, selected a login and a password using bruteforce and then disabled the iptables utility controlling the firewall after successful authorization on the server. Then the attackers uploaded the miner utility and the configuration file to the compromised server. Some time later, they started using malware for this purpose. In August, virus analysts discovered the
Having investigated the server where this malware was downloaded from, our experts discovered Trojans with similar functions for Microsoft Windows. Read more about this incident in the article on our website.
In November, we discovered another Linux miner dubbed
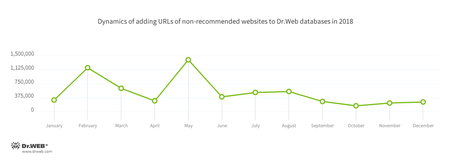
Dangerous and non-recommended websites
Parental (Office) control and SpIDer Gate databases are regularly updated with new addresses of non-recommended and potentially dangerous websites. There are fraudulent and phishing resources, as well as malware distributing pages. This year’s trends for adding information to these databases is shown in the diagram below.
Network fraud
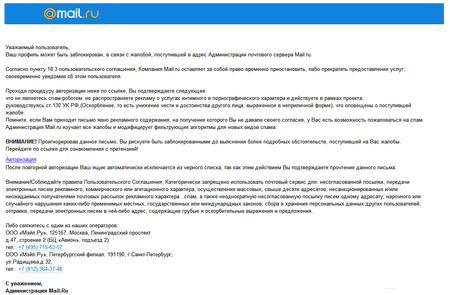
Internet fraud is a very common criminal business. In 2018, online criminals remained notably active. In early March, were detected bulk phishing emails, allegedly sent on behalf of the Mail.Ru Group. The attackers wanted to obtain the credentials of the Mail.Ru email server users; and thus used a fake website, which mimicked the design of this popular email service.
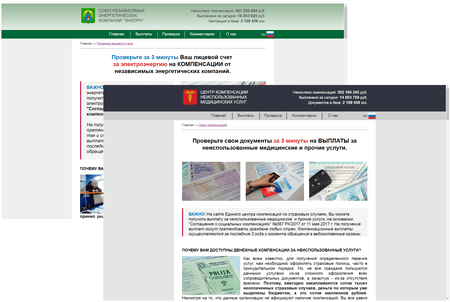
In May, we told our readers about another online fraud mechanism, which took advantage of generous offers for social benefits. The victims were lured to specifically created websites by spam and bulk text messages. Once there, they were offered an opportunity to receive refunds for overpayed public utilities, medical services, or compulsory insurance. To get the money, the criminals demanded a small sum be transferred to their account. Of course, no refunds was given to users who transferred the money.
Doctor Web experts revealed more than 110 similar websites between February and May 2018. In August, the attackers began sending letters to domain administrators registered with the RU-CENTER hosting provider. The cybercriminals demanded money for renewing soon-expiring domains, but indicated the details of their own Yandex.Money wallet instead of the official banking details of RU-CENTER.
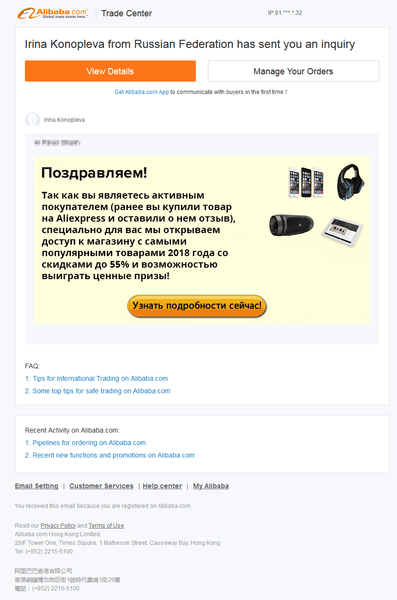
Attackers often send emails on behalf of well-known companies. The popular Aliexpress online store was no exception. The criminals invited its regular customers to visit a special online store with numerous discounts and gifts.
The “store” was actually a page with links to various fraudulent marketplaces that sold substandard goods or goods at inflated prices. We are still not sure how the attackers managed to accumulate a database with the contact information of real Aliexpress customers.
Mobile devices
In the past year, Android device users were bombarded with malware. The list included banking Trojans trying to steal money from the users from Russia, Turkey, Brazil, Spain, Germany, France, and other states. In spring, virus analysts discovered the Trojan
In November, Doctor Web experts investigated the software
In December, we detected the Trojan
Throughout the year, virus writers were actively spreading Android bankers, based on the open source code of the Android Trojan
A lot of banking malware ended up on devices thanks to Trojan downloaders such as,
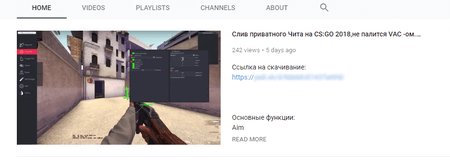
In 2018, Android users were again targeted by Trojans of the


Another Trojan of this family, added to the Dr.Web virus database as
To obtain money illegally, cybercriminals used other malicious programs as well, including Trojan miners such as
In autumn, Doctor Web experts discovered the
Virus writers actively used Trojans for fraudulent purposes. A popular scheme in 2018 was to offer of reward for participating in polls. When launched, such Trojans displayed a webpage created by the attackers. There, potential victims were asked to answer a few questions. To get money from users, some kind of verification or other form of payment was required; but after sending the funds, the users of the infected devices did not receive anything. Clicker malware that opened websites with ads and automatically clicked on them were also popular. See more details in the article.
Another type of fraud was to subscribe owners of Android mobile devices to expensive services. Trojans such as
In the year 2018, new cases of Android firmware infection were detected. We reported one of them in March. Virus analysts detected the Trojan
Prospects and possible trends
Even though 2018 saw no serious virus outbreaks, new waves of bulk distribution are quite possible in the future. The number of malicious scripts in various languages will continue to grow. Such scripts will not only target devices running Microsoft Windows, but also other systems, specifically Linux.
New Trojans for covertly mining cryptocurrency using the hardware of infected devices will appear as well. Cybercriminals are likely to remain interested in the Internet of Things, too. Trojans for smart devices already exist, but their number will surely grow in the near future.
There is also strong reason to believe that virus writers will be creating and distributing new Trojans for Google Android in 2019. This year’s trends have demonstrated that advertising and banking Trojans will most likely be prevalent among mobile malware.
Finally, the number of fraudulent emails is unlikely to decrease. Online fraudsters will continue inventing new ways to deceive Internet users. Be that as it may, new threats to information security will certainly appear in the coming year. This means it is very important to provide reliable and up-to-date antivirus protection for our devices.








![[You Tube]](https://st.drweb.com/static/new-www/social/youtube.png)
![[Twitter]](https://st.drweb.com/static/new-www/social/twitter.png)
![[Facebook]](https://st.drweb.com/static/new-www/social/facebook.png)
![[Instagram]](https://st.drweb.com/static/new-www/social/instagram.png)
![[Spiceworks]](https://st.drweb.com/static/new-www/social/spiceworks.png)