Doctor Web’s October 2018 virus activity review
[% DEFAULT FILE_REVIEW = ''; NAME_SOME_ARRAY_IN_MACROSNAME = [ { box => "Overview" }, { box => "Threat of the month" }, { box => "Statistics" }, { box => "Encryption ransomware" }, { box => "Dangerous websites" }, { box => "Mobile devices" } ] %] [% BLOCK global.tpl_blueprint.content %]
October 31, 2018
In October, Doctor Web announced the results of an investigation into online scamming. Over 10,000 people fell victim to a cybercriminal, who gained a total of $24,000.
For a month, the attackers kept sending emails soliciting money from users and threatening to compromise their personal data. Apparently, the scammers managed to get ahold of several databases with registration data, including email addresses and passwords. The attackers used the addresses to send messages stating that they knew victims’ password and had allegedly installed malware on their computers. To prevent victims’ personal details from becoming public, the cybercriminals demanded a $500-$ 850 bitcoin ransom.
The scammers are actively using several bitcoin wallets; and, judging by the information on blockchain.com, several users have already fallen for the fraud.
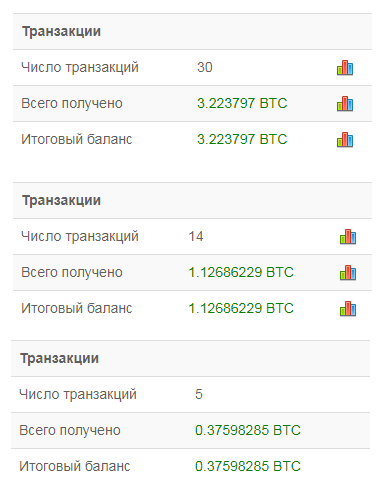
This method for extorting money has recently been extremely popular among cybercriminals. They send emails with various threats, but with limited combinations of email addresses and passwords. Of course the scammers did not use any viruses or Trojans to extract this information. Users simply needed to change the passwords to protect themselves.
Principal trends in October
- Exposing the activities of a dangerous cybercriminal
- Mass money recovery spamming to Internet users
Threat of the month
Doctor Web experts have conducted a large-scale investigation. The results were published this October. Our malware analysts have analyzed the activities of cybercriminals who went by the names Investimer, Hyipblock, and Mmpower. To achieve their goals, they used a wide range of malware, including stealers, downloaders, backdoors, and a Trojan miner with an embedded module replacing the contents of the clipboard.
Investimer focused primarily on cryptocurrency fraud. The range of methods used to siphon money was quite wide. For example, it created fake cryptocurrency exchange websites, mining farms, affiliate programs offering rewards for viewing ads, and online lotteries.
The general scheme the cybercriminal used to deceive users is as follows: the potential victim is, by various means, lured to a fraudulent website that requires the download of a certain client program to use it. However, instead of a client program, the victim downloads a Trojan that installs other malware on the computer when the attacker signals it. These programs (mainly stealer Trojans) steal confidential data from affected devices, and the scammer later uses it to steal cryptocurrency and money from victims’ accounts through various payment systems.
Doctor Web analysts believe the total number of users affected by Investimer’s illegal activities exceeds 10,000. Our experts estimate the damage to victims as over $23,000, in addition to more than 182,000 Dogecoins, equal to about $900 at the current rate. You can read more on this investigation in this article on our website.
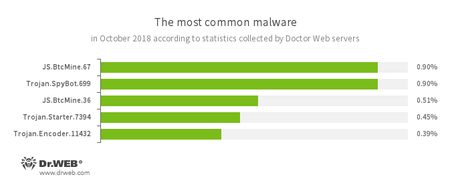
According to Doctor Web’s statistics servers
JS.BtcMine - A family of JavaScript scenarios designed to covertly mine cryptocurrencies (mining).
Trojan.SpyBot.699 - Trojan spyware designed for keyboard clickjacking on an infected device, executing commands and stealing confidential information.
- Trojan.Starter.7394
- A Trojan whose main purpose is to launch an executable file with a specific set of malicious functions in an infected system.
Trojan.Encoder.11432 - An encryption worm, also known as WannaCry.
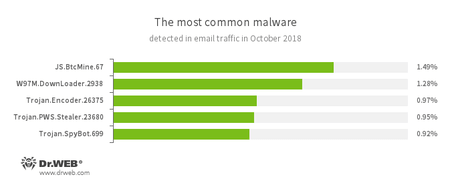
Statistics for malware discovered in email traffic
JS.BtcMine - A family of JavaScript scenarios designed to covertly mine cryptocurrencies (mining).
W97M.DownLoader - A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised computer.
- Trojan.Encoder.26375
- An encryption ransomware Trojan that encrypts files and demands a ransom to decrypt the compromised data.
Trojan.PWS.Stealer - A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
Trojan.SpyBot.699 - Trojan spyware designed for keyboard clickjacking on an infected device, executing commands and stealing confidential information.
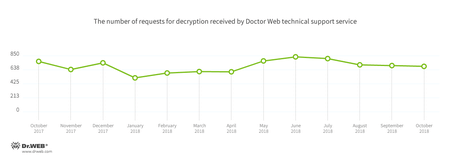
Encryption ransomware
In October, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
Trojan.Encoder.858 — 20.04% of requests;Trojan.Encoder.11464 — 11.67% of requests;Trojan.Encoder.567 — 6.23% of requests;- Trojan.Encoder. 25574 — 5.84% of requests;
- Trojan.Encoder.1539 — 4.86% of requests;
Trojan.Encoder.5342 — 1.75% of requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During October 2018, the URLs of 156,188 non-recommended websites were added to the Dr.Web database.
| September 2018 | October 2018 | Dynamics |
|---|---|---|
| + 271,605 | + 156,188 | - 42.49% |
Malicious and unwanted programs for mobile devices
In early October, an entry was added to the Dr.Web virus databases to detect the Android banker
At the end of the month, Google Play was found to have the downloader Trojans
The following October events related to mobile malware are the most noteworthy:
- the detection of malicious applications on Google Play;
- distribution of a dangerous banking Trojan capable of compiling and executing malicious code on the go.
Find out more about malicious and unwanted programs for mobile devices in our special overview.




![[You Tube]](https://st.drweb.com/static/new-www/social/youtube.png)
![[Twitter]](https://st.drweb.com/static/new-www/social/twitter.png)
![[Facebook]](https://st.drweb.com/static/new-www/social/facebook.png)
![[Instagram]](https://st.drweb.com/static/new-www/social/instagram.png)
![[Spiceworks]](https://st.drweb.com/static/new-www/social/spiceworks.png)