SHA1
- 1b41c5e14f17d3a695c94fcbe696294ec0bc96f2 (dmg)
- a6a6d0050d9ac5d69eef7228cfd0fb4480e06bb1 (mach-o)
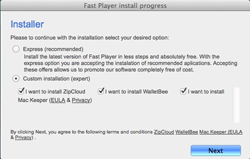
An installer of unwanted applications that targets OS X. Once launched, it reads the ".payload” file in the application folder. The installer also contains another "payload” file, but it is not used. The file looks as follows:
host|hex-encoded jsonJSON format:
{
"publisher": "790",
"uid": "14375585952507RhhhlENdR",
"campaign": "1882",
"extra": {
"ttbpromo": "DDL",
"ttbaff": "54ec7d5f5f1c1e2452000008",
"nrid": "14375585952507RhhhlENdR",
"ip": "213.***.**.60",
"tt": "aac2d73c437d76f03ba0609d4e2a6bcae556aa8e",
"ttbtt": "ddl",
"lpd": "www.best*****pp.com",
"ttbhash": "IP1lNCYV",
"requestHost": "admin.best*****file.com",
"ttbvar": "",
"referer": "",
"build": "469",
"time": "2015/07/22 10:49:55",
"ttbts": "55759fba5f1c1e6c39000000",
"userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.118 Safari/537.36",
"fileName": "MPlayer",
"osVersion": "0",
"os": "MacOSX",
"browser": "ch"
},
"url": "",
"usedBrowser": "ch",
"sign": "sm1",
"caption": "",
"host": "domain.com",
"carrier": "FastPlayerMac"
}Once launched, the installer replaces a subdomain of the C&C server with the “api” value. For instance, if in the configuration file the URL is admin.best*****file.com, the address of the C&C server will beapi.best*****file.com".
In order to get the list of applications for download prompting, the installer creates URL and encrypts it using the key randomly generated. For encryption the AES algorithm is used in СВС mode. Then, the following line is created:
hexencode(iv+key+encoded_url)After that, the following request is made:
http://api.<domen>/<hexencoded>The node URL from which the applications will be downloaded is created the following way:
http://api.<domen>/stan/api/<publisher>/<campaign>/<carrier>/<language>/<region>/?browser=<browser>&ip=<ip>The following fields are retrieved from the configuration file:
publisher
campaign
carrier
ip
browserThe following values can be used as a parameter of the “browser” variable:
["ff", "ch", "sf","op"]The rest fields are updated with data that is identified based on the operation system parameters.
The server response is also encrypted with the key included in the installer’s body and contains the programs list which can be downloaded to the user’s Mac. The response has the following main fields:
- id - an identifier of the installed application. There are minimum 736 applications judging by the existing ids.
- score - the “rate” of an application. Since the maximum number of applications that can be prompted to install is limited, every application gets some “rate”. Then the installer tries to create an optimal list of compatible software with the highest “rate”.
- appUrl - the address for file download.
- restrictions - the id list of those applications that cannot be installed along with the current one. For example, the MacKeeper application will not be installed along with the MacKeeper Grouped application.
For every application, three fields that contain JavaScript encrypted with Base64 are determined:
- preCheck - checks if the application is already installed;
- macBehavior - the code for installation;
- postCheck - checks if the installation was completed successfully.
The installation dialog has the Custom Installation mode, which shows check boxes that allow to refuse all the additional software.