A multipurpose backdoor that can execute various commands coming from the remote server.
The module responsible for the backdoor's installation and its bootkit features was borrowed from the Trojan.Mayachok family of malicious programs. However, virus makers introduced a number of significant changes to the source code.
- Original Trojan.Mayachok generated a unique VBR code which was used to create another build of the malware. In the case of BackDoor.Gootkit.112, all functions are compiled in the dropper that alters the Volume Boot Record (VBR) code during the infection process.
- To compress the modules of Trojan.Mayachok, the aplib library was used. BackDoor.Gootkit.112 is decrypted and extracted using RtlDecompressBuffer (COMPRESSION_FORMAT_LZNT1).
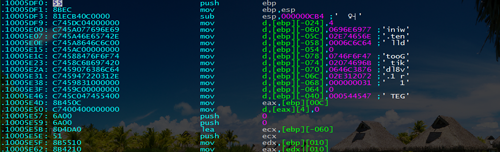
- The driver, to which VBR transfers control prior to system initialization, was also taken from the source code of Trojan.Mayachok, but the code was partially rewritten; so most of the pointers (various tables and a shellcode for injections) became position independent for unknown reasons. For example, the following routine to retrieve an address:
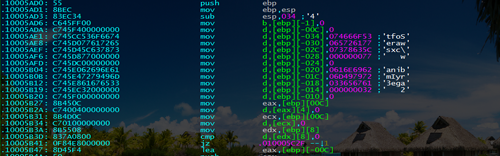
Another example is related to string generation. The routine looks as follows:get_shellcode2 proc near ; CODE XREF: csrss_inject+67p .text:10006645 E8 00 00 00 00 call $+5 .text:1000664A 58 pop eax .text:1000664B 83 C0 05 add eax, 5 .text:1000664E C3 retn .text:1000664E get_shellcode2 endp .text:1000664E .text:1000664F ; ========= S U B R O U T I N E =========================== .text:1000664F ; Attributes: noreturn bp-based frame .text:1000664F .text:1000664F shellcode2 proc near
However, some pointers remained intact. In particular, one of them refers to the following quotation by Homer Simpson: “Just pick a dead end and chill out till you die”, which is output in the debugger once initial initialization of the loader is complete..text:10003B0B push ebp .text:10003B0C mov ebp, esp .text:10003B0E sub esp, 78h .text:10003B11 call get_api_table .text:10003B16 mov [ebp+pAPITable], eax .text:10003B19 cmp [ebp+pAPITable], 0 .text:10003B1D jz no_apitable .text:10003B23 mov dword ptr [ebp+szRegistryPath], 52005Ch ; REGISTRY\MACHINE\CURRENTCONTROLSET\SERVICES\null .text:10003B2A mov dword ptr [ebp+szRegistryPath+4], 470045h ; .text:10003B31 mov dword ptr [ebp+szRegistryPath+8], 530049h ; .text:10003B38 mov dword ptr [ebp+szRegistryPath+0Ch], 520054h ; .text:10003B3F mov dword ptr [ebp+szRegistryPath+10h], 5C0059h ; .text:10003B46 mov dword ptr [ebp+szRegistryPath+14h], 41004Dh ;
The Gootkit name can be found in both the loader and the payload module code.
In addition, all driver components responsible for its interaction with other modules operating in user mode were also removed—in particular, the driver that allowed those modules to use VFS. However, BackDoor.Gootkit.112 still has features responsible for VFS initialization and protection.
Unlike Trojan.Mayachok whose payload was incorporated into the loader, BackDoor.Gootkit.112 stores information on payload modules in the HKLM\SOFTWARE\CXSW registry branch as binaryImage32 or binaryImage64, depending on the OS platform (32-bit or 64-bit).
To retrieve the payload, BackDoor.Gootkit.112 injects a special shellcode into SERVICES.EXE, EXPLORER.EXE, IEXPLORE.EXE, FIREFOX.EXE, OPERA.EXE, and CHROME.EXE. The main purpose of the injected shellcode is to download the payload module from the system registry or from a remote server on the Internet. Payload binary files are compressed and encrypted.
Bypassing UAC
To bypass UAC (User Accounts Control) and elevate its own privileges, BackDoor.Gootkit.112 uses a shim (Microsoft Windows Application Compatibility Infrastructure). The Trojan employs the SQL Server Client Network Utility (cliconfg.exe) whose manifest file has the AutoElevate attribute set to “true”; thus, Windows elevates privileges for such applications without involving UAC.
BackDoor.Gootkit.112 uses the apphelp.dll library (SdbCreateDatabase, SdbDeclareIndex, SdbWriteStringTag, and so on) to create a database. The Trojan generates the database name and the value of the Application parameter randomly.
...
if(!SdbWriteStringTag(hDb, TAG_NAME, szAppName))
break;
if(!SdbWriteStringTag(hDb, TAG_APP_NAME, SHIM_APP_NAME))
break;
if(!SdbWriteStringTag(hDb, TAG_VENDOR, _T("Microsoft")))
break;
...
SdbWriteStringTag(hDb, TAG_COMPANY_NAME, _T("Microsoft Corporation"));
SdbWriteStringTag(hDb, TAG_INTERNAL_NAME, szAppName);
SdbEndWriteListTag(hDb, listMatch);
TAGID listShim = SdbBeginWriteListTag(hDb, TAG_SHIM_REF);
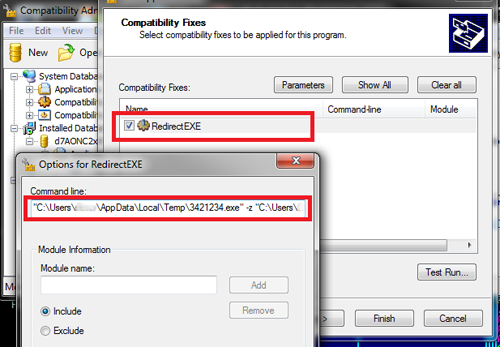
SdbWriteStringTag(hDb, TAG_NAME, _T("RedirectEXE"));
SdbWriteStringTag(hDb, TAG_COMMAND_LINE, szTargetApp);
SdbEndWriteListTag(hDb, listShim);
...
The RedirectEXE shim is used to load the Trojan. This shim allows to run a modified version of a specified application or the malicious program itself instead of the original executable file. BackDoor.Gootkit.112 employs RedirectEXE parameters to specify the path to its executable and a link to the created database.
Once the database is created, it gets installed on the system by means of sdbinst.exe whose manifest file has also the AutoElevate parameter set to “true”; so this utility runs with special privileges. Overall, the UAC bypass scheme looks as follows:
- The Trojan creates and installs a new database (shim).
- Then it launches cliconfg.exe with elevated privileges.
- The shim unloads the original process and uses RedirectEXE to launch the Trojan.
Payload
The Trojan's payload is implemented as an executable file of about 5 MB written in C++. Most of this file is a JavaScript interpreter known as Node.JS. The executable file contains more than 70 pieces of JavaScript code; a significant portion of them constitutes the Node.JS core that provides an easily accessible interface to work with native objects. Some scripts incorporate the Trojan's payload; they enable the backdoor to execute commands coming from the remote server and download additional modules stored in the Windows registry (together with the main module of BackDoor.Gootkit.112).
The Trojan can execute the following commands:
- Intercept HTTP traffic
- Perform web injections
- Block specific URLs
- Take screenshots
- Acquire the list of running processes
- Acquire the list of local users and groups
- End specified processes
- Execute shell commands
- Launch executable files
- Update itself
In addition to that, BackDoor.Gootkit.112 can perform some other commands.