SHA1 hash:
- baab225a50502a156222fcc234a87c09bc2b1647
Description
A trojan app written in the C++ programming language and designed for computers running Microsoft Windows. It launches BackDoor.Spy.4038, malware that is encrypted and stored in its body, on the infected system.
Operating routine
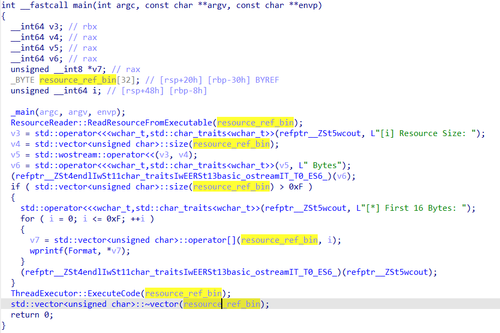
Trojan.Siggen31.54011 loads the ref.bin resource stored in its body into the RAM:
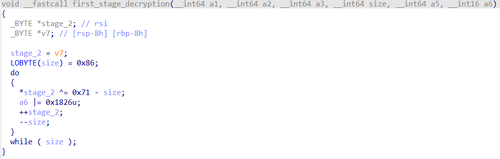
Next, it decrypts part of the data, using the following algorithm:
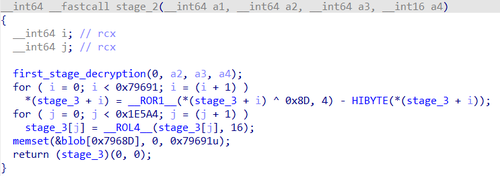
The output is a shellcode for decrypting the binary data array (BLOB):
After that, the code uses the hash value to obtain the functions necessary for the payload to work; using the XOR operation, the code decrypts the payload from its body. At the same time, a separate data BLOB is stored in the RAM. During the course of Trojan.Siggen31.54011’s operation, specific values are taken from this BLOB and assigned to each variable (e.g., for the memory address containing a data array for decryption, for the encryption key, for the number of bytes, etc.).
The payload continues to use the same BLOB. Using the XOR operation, the payload decrypts the target executable file from its body (BackDoor.Spy.4038) and runs it in a separate thread.
BackDoor.Spy.4038 connects to the C2 server via a reverse shell and waits for incoming commands. The received commands are executed using the cmd.exe command-line interpreter: