sha1:
- 94d25cebb6ba408c7c45bd12fd8aca5293d5df21
Description
A backdoor written in Kotlin and targeting Android-based devices. It performs a large number of malicious actions when commanded by attackers and is used to steal confidential data and engage in cyber espionage. This malicious app is distributed under the guise of anti-viruses and targets Russian users.
Operating routine
When operating, Android.Backdoor.916.origin pretends to perform an anti-virus scan on a device. The probability of “detecting” threats is hardcoded into it. The more time that has passed since the last “scan”, the higher the chance is, but no more than 30%. The following algorithm is used:
long v = scanDataStore6.getLastScanTime();
if(new Random().nextDouble() >= Math.min(((double)(v <= 0L ? 24L : (System.currentTimeMillis() - v) / 3600000L)) / 100.0, 0.25) + 0.05) {
z = false;
}
The number of allegedly detected threats is determined randomly and ranges from 1 to 3.
Launching
When it first launches, Android.Backdoor.916.origin requests the following system permissions:
- Access to geolocation;
- Access to audio recording;
- Access to SMS, contacts, call history, media files, permission to make phone calls;
- Access to the camera (for taking pictures and recording video);
- Permission to run in the background;
- Device administrator rights;
- Access to Accessibility Service.
The backdoor launches a coroutine (a background task) that checks the state of the services every minute, launching them again if needed:
- DataSecurity
- SoundSecurity
- CameraSecurity
- SecurityDisplay (in more recent versions, e.g., 5059c6dc5a657722e3c13f720cbf77e9b58ef515)
The DataSecurity service
Connects to the C2 server via a socket and can execute the following commands:
- ACTIVATE_APP_PROTECTION — to send an intent ru.next.secure.ACTION_PROTECTION_CHANGED and assign the value true to parameter enabled;
- DEACTIVATE_APP_PROTECTION — to send an intent ru.next.secure.ACTION_PROTECTION_CHANGED and assign the value false to parameter enabled;
- CHECK_APP_PROTECTION — to check the status of the backdoor’s self-protection;
- REQUEST_LOGS — to upload the contents of the backdoor’s log file to the C2 server;
- CLEAR_LOGS — to clear the log file;
- LOGGING_ENABLE — to enable logging;
- LOGGING_DISABLE — to disable logging;
- GET_CONTACTS — to upload the contact list to the C2 server;
- GET_GALLERY — to upload all images stored on the SD card to the C2 server;
- GET_GALLERY_RANGE — to upload images of a given range of values from the SD card to the C2 server;
- GET_GALLERY_IMAGE — to upload a particular image stored on the SD card to the C2 server;
- GET_BATTERY_INFO — to upload the battery’s technical data to the C2 server (percentage, is_charging, plugged, charge_type, temperature, voltage, and health);
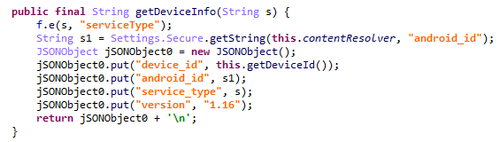
- GET_DEVICE_INFO — to upload the device’s technical data to the C2 server (manufacturer, version, product, model, brand, device, host, sdk, fingerprint, hardware, board, and securityPatch);
- getSMS — to upload all incoming SMS to the C2 server (with the type inbox) and outgoing SMS (with the type sent);
- GET_CALL_LOGS — to upload the phone call history to the C2 server;
-
GET_SIM_INFO — to upload the SIM card information to the C2 server. Depending on the OS version, the backdoor uploads:
- displayName, carrierName, countryIso, number;
- operatorName, countryIso, simState, number, imei.
- GET_NETWORK_INFO — to upload information about the network and the device’s interfaces to the C2 server (ipv4_address, name, mac_address, and display_name);
- GET_LOCATION — to upload geolocation data to the C2 server (latitude, longitude);
- RUN_SHELL — to execute the received shell command and send the result back to the socket.
The SoundSecurity service
It connects to the C2 server via a socket and can execute the following commands:
- START_AUDIO — to start streaming audio from the device’s microphone;
- STOP_AUDIO — to stop streaming.
The CameraSecurity service
It connects to the C2 server via a socket and can execute the following commands:
- START_VIDEO — to start video streaming from the device’s camera;
- STOP_VIDEO — to stop streaming;
- SET_QUALITY — to change the streaming video quality.
The SecurityDisplay service
It connects to the C2 server via a socket and can execute the following commands:
- START_SCREEN — to start screencasting;
- STOP_SCREEN — to stop screencasting.
The keylogger and the theft of program content
Android.Backdoor.916.origin uses the Accessibility Service to execute keylogger functionality to hijack content from messengers and browsers. The trojan monitors the following apps:
- org.telegram.messenger — Telegram
- org.telegram.messenger.web — Telegram
- com.android.chrome — Google Chrome
- com.google.android.gm — Gmail
- ru.yandex.searchplugin — Яндекс Старт (Yandex Start)
- com.yandex.browser — Яндекс Браузер (Yandex Browser)
- com.whatsapp — WhatsApp
In addition, it monitors the presence of a particular text on the screen—for example, далее, submit, отправить, sign in, войти and log in.
The data obtained by the backdoor is sent to the service DataSecurity, which uploads it to the C2 server.
Self-protection
Android.Backdoor.916.origin uses Accessibility Service to monitor the device’s screen. It checks whether the user is in the program’s information window or in one of the sections of the program control menu. If the backdoor detects an attempt to uninstall it or change the settings, it instantly returns the user to the main screen, blocking the action.
Information about such an attempt is also uploaded to the C2 server with the message type UNINSTALL_ATTEMPT and one of the following reasons:
- delete_confirmation_detected
- app_info_with_uninstall_buttons
- app_info_screen_detected
- app_management_with_our_app
- system_security_screen_with_our_app
Data transfer
Each Android.Backdoor.916.origin service uses its own port to upload data to the C2 server. The following ports are specified in the trojan:
- port — 10000 — is not used;
- audioPort — 10001 — is used by the service SoundSecurity;
- functionPort — 10002 — is used by the service DataSecurity;
- screenPort — 10003 — is used by the service SecurityDisplay;
- videoPort — 10004 — is used by the service CameraSecurity.
After establishing the connection with the socket, the data is uploaded in the following format:
The transmitted string is converted to bytes.
The parameter serviceType is a service type. It depends on the class that connects to the socket and can have the following values:
- sms
- video
- screen
- audio
- The separator string BEGIN_MSG\n at the beginning of the message is sent, encoded into bytes.
- The JSON object containing data is sent; this object is preliminarily converted into a string that is encoded into bytes.
- The separator string \nEND_MSG\n at the end of the message is sent, also encoded into bytes.
Communicating with the C2 server
Android.Backdoor.916.origin has a configuration containing a list of C2 servers consisting of dozens of positions. This data is stored in separate classes bearing the following names:
- DneprIPs
- KievIPs
- BerdikIPs
- SkovorodkaIps
- TeslaIP
- TwoFlorIPs
- OsnovaIPs
- OdessaIPs
- TwoFlorIPs
- GeneveIPs
- NikoIPs
- SixFlorIPs
- PoltavaIPs
- AlekseevIPs
- KabanovIPs
To change the C2 server address, the trojan can switch between hostings (switchCity). However, this functionality is not being used in the discovered trojan samples.
MITRE matrix
|
Stage |
Technique |
|---|---|
|
Initial Access |
Phishing (T1660) |
|
Execution |
Command and Scripting Interpreter: Unix Shell (T1623.001) |
|
Persistence |
Event Triggered Execution (T1624) Broadcast Receivers (T1624.001) Foreground Persistence (1541) |
|
Privilege Escalation |
Abuse Elevation Control Mechanism (T1626) Device Administrator Permissions (T1626.001) |
|
Defense Evasion |
Foreground Persistence (T1541) Impair Defenses (T1629) Prevent Application Removal (T1629.001) |
|
Credential Access |
Keylogging (T1417.001) |
|
Discovery |
File and Directory Discovery (T1420) Location Tracking (T1430) System Information Discovery (T1426) System Network Configuration Discovery (T1422) |
|
Data Collection |
Archive Collected Data (T1532) Audio Capture (T1429) Data from Local System (T1533) Keylogging (T1417.001) Location Tracking (T1430) Protected User Data (T1636) Call Log (T1636.002) Contact List (T1636.003) SMS (T1636.004) Screen Capture (T1513) Video Capture (T1512) |
|
Command and Control |
Non-Standard Port (T1509) |
|
Exfiltration |
Exfiltration Over C2 Channel (T1646) |