Packer: absent
Compilation date: 2021-29-03
- SHA1 hash: abfd737b14413a7c6a21c8757aeb6e151701626a
Description
A multi-functional backdoor trojan for 64-bit and 32-bit operating systems of the Microsoft Windows family. Designed to establish an encrypted connection with the command and control server and unauthorized control of an infected computer. It has the functions of a file manager and Remote Shell.
Preparing procedures
At the beginning of the work, the backdoor decrypts the overlay provided by the shellcode. The first encryption layer is removed by the following algorithm:
k = 0x37
s = bytearray()
for i in range(len(d)):
c = d[i] ^ k
s.append(c)
k = (k + c) & 0xff
The second layer is the XOR operation with the key 0xCC.
This overlay contains:
- configuration of trojan;
- module for bypassing UAC.
Configuration looks as follows:
struct st_proxy
{
char proxy_addr[32];
char proxy_login[64];
char proxy_password[64];
_BYTE pad[2];
};
struct st_config
{
char cnc_addr[4][34];
st_proxy proxies[4];
char home_dir[260];
char exe_name[50];
char loader_name[50];
char shellcode_name[50];
char software_name[260];
char startup_argument[50];
_DWORD reg_hkey;
char reg_run_key[200];
char reg_value_name[52];
char taskname[52];
_DWORD mstask_mo;
char svcname[50];
char svcdisplayname[50];
char svcdescription[256];
char reg_uninstall_key[50];
char inject_target_usr[260];
char inject_target[260];
_BYTE byte0[2];
_BYTE flags;
_BYTE pad[3];
_DWORD keepalivetime;
unsigned __int8 key[16];
};
The flags field displays which autoload methods the trojan should use, as well as what launch features are:
enum em_flags
{
GOT_ENOUGH_RIGHTS= 0x1,
UNK_FLAG_2 = 0x2,
UNK_FLAG_4 = 0x4,
INSTALL_AS_MSTASK = 0x8,
INSTALL_AS_SERVICE = 0x10,
RUN_WITH_ARGUMENT = 0x20,
INJECT_TO_PROCESS = 0x40,
RUN_AS_USER = 0x80,
};
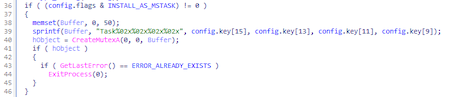
If the launch is specified via the task scheduler ([string]INSTALL_AS_MSTASK[/string]), then after decrypting the configuration [string]flags[/string] creates a mutex to prevent restart:
Next, it checks if the trojan has enough rights to launch in the way that was previously specified in the configuration. If not, then it restarts itself bypass UAC.
Trojan checks for the presence of a file in the path C:Users\Public\Downloads\clockinstall.tmp, and if it exists, it deletes clockinstall.tmp.
If the clockinstall.tmpfile is missing, then it checks if the install file exists in the folder from which the Trojan was launched and removes it if it exists.
Then installs itself into the system in accordance with the type specified in the configuration. In addition, the backdoor will try to hide its activity from the user.
If the Trojan runs on a 32-bit OS, then the same mechanism for hiding a service from running ones is valid, as inBackDoor.PlugX.28, - deleting that structure from the list of [string]ServiceDatabase[/string] structures, which corresponds to the trojan service.
If the configuration specifies that the Trojan should be injected into a process, then it will be injected into the target process. If the [string]RUN_AS_USER[/string] flag is specified in the configuration, then the Trojan will wait until at least one authorized user appears, after which it will create its own process, but on behalf of the user.
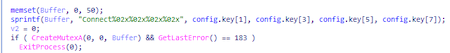
Regardless of the trojan's autorun type, only one process can communicate with the command and control server. This creates a mutex:
Before attempting to establish a connection with the command and control server, trojan determines the proxy server settings. For this purpose:
- The presence of the [string]<process_name>.ini[/string] file in the folder from which the Trojan process was launched is checked. Example of the configuration:
[AntiVir] Cloud=0A0804D22420000000000000000000000000000000000000000000000000000000000000000000000000000000000000299CC1003C9CC10098F11900DCF1190062F2190000000000E02AC300CC004501D8F1190000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001 - Reads a file named [string]<loader_name>.tmp[/string] in the Trojan folder, where [string]<loader_name>[/string] is the value from the configuration;
- Reads proxy settings from registry [string][HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings][/string], keys [string]ProxyEnable[/string] and [string]ProxyServer[/string]
- Reads proxy settings from Mozilla Firefox settings - [string]%APPDATA%\Mozilla\Firefox\<profile>\prefs.js[/string]
- Also checks for stored login:password from the proxy server in Mozilla Firefox and Internet Explorer.
Control server protocol
Establishing a connection to the server mimics the creation of a TLS1.0 connection between the client and the server. Trojan body contains two buffers:
- Contains the TLS1.0 Client Hello package:
- Contains TLS 1.0 Client Key Exchange packets with key length [string]0x100[/string] bytes, Change Cipher Spec, Client Handshake Finished:
When sending a Client Hello packet, the trojan encrypts all bytes of the Client Random field, starting from the 4th one, using the XOR method with random bytes, and records the current time in the first 4. The server's response to this message is accepted, but the data is ignored.
When sending the second packet, the backdoor also encrypts the public key field of the Client Key Exchange packet using the XOR method with random bytes, and writes its 28-byte key into the data of the Client Handshake Finished packet, which will be used to encrypt and decrypt packets sent or received from the server . The backdoor encrypts the last 4 bytes of the Client Handshake Finished packet with random bytes and sends it to the command and control server. In response, the server sends its own key, which is used to initialize the key shared with the client.
After that, the backdoor enters the command processing cycle from the control server. The traffic between the client and the server is encrypted using the [string]RC4[/string] algorithm.
The list of commands:
| opcode | Command |
|---|---|
| 0x01 | Gathering information regarding the infected device |
| 0x02 | Remote shell |
| 0x03 | File manager (see below for commands ending in 3) |
| 0x100 | Keep-Alive |
| 0x103 | Open file for writing |
| 0x203 | Download a file |
| 0x303 | Data to be written |
| 0x400 | Reconnect to server |
| 0x403 | Obtain information about disk or directory listing; |
| 0x500 | To finish work |
| 0x503 | Move a file; |
| 0x600 | Delete proxy configuration ini file |
| 0x603 | Delete a file |
| 0x703 | Run a process; |
| 0x700 | Execute a command during ShellExecute |
| 0x800 | Renew configuration |