Packer:
Packer
Compilation date:
19:36:04 28.08.2017
SHA1 hash:
736d8e03e40e245d4c812b091b5743fce855a529
Description
A malicious DLL installed on targeted computers by the BackDoor.Farfli.122 trojan. It is written in C++ and supports 32-bit and 64-bit Microsoft Windows operating systems. This library represents a backdoor that receives commands from attackers and allows them to remotely control the infected computers.
Operating routine
The library is loaded into the memory by BackDoor.Farfli.122. It exports the mystart function that contains the main malicious functionality. This library has a PcMain.exe name in the exporting table.
mystart function
Upon receiving control from the shellcode loaded by BackDoor.Farfli.122, BackDoor.Farfli.125 performs various checkups. At the beginning, the trojan determines if it has been launched through the Wow64 subsystem and runs in the 64-bit environment. With that, if the IsWow64Process function execution returns an error, it displays a MessageBox with the x1 text. Next, BackDoor.Farfli.125 checks whenever the module file name has \explorer.exe or \internet explorer\iexplore.exe in it.
If the backdoor runs in the context of the explorer.exe or IE process, it creates a hidden directory C:\Microsoft\TEMP\Networks\Connections\Pbksn. Next, it verifies the module file name has a nvdiassnx string and tries to create a nvdiassnx folder in the directory it created earlier. If the trojan does not run from the nvdiassnx folder, it creates a file with the RasTls
If the backdoor does not run in the context of the explorer.exe or IE process, it creates a C:\Microsoft\TEMP\Networks\Connections\Pbksn\nvdiassnx\ky3log.dat file.
Anchoring in the system
Upon completing the initial preparation, the trojan checks if it runs in the context of the explorer.exe or iexplore.exe process and if it was launched from the ...\nvdiassnx directory.
-
Operation in the context of the explorer.exe or iexplore.exe process
If it runs in the context of the explorer.exe or iexplore.exe process, BackDoor.Farfli.125 immediately proceeds to its main malicious functionality. Otherwise, it verifies if it runs from the ...\nvdiassnx.
-
Operation from the nvdiassnx directory
If the trojan was not launched from the ...\\nvdiassnx directory, it checks if the Global\\vssafuyuhdw332kjgtts1 event is present. If it exists, it terminates its process to ensure only one copy of the trojan is launched. Otherwise, the trojan moves its components ― RasTls.exe, RasTls.dll and RasTls.dat ― to the C:\Microsoft\TEMP\Networks\Connections\Pbksn\nvdiassnx directory.
Its further actions depend on the operating system version.
If BackDoor.Farfli.125 is running on Windows Vista and later Windows versions, the RasTls.exe module is set to autorun through the [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce] registry key. Next, the trojan launches the iexplore.exe process with the CREATE_SUSPENDED flag, reads the shellcode from the RasTls.dat file, decrypts and injects it into the iexplore.exe process, launched earlier, continuously using the VirtualAllocEx, WriteProcessMemory and ResumeThread functions. Herewith, it patches the entry point of the process so the injected shellcode will receive control.
If BackDoor.Farfli.125 is running on a Windows version below Windows Vista and not through the Wow64 subsystem, the trojan performs the same actions but injects the shellcode into the explorer.exe process.
If the trojan is launched from the ...\\nvdiassnx directory, it performs the same actions described earlier, excluding the Global\\vssafuyuhdw332kjgtts1 event check and moving files.
Main functionality
BackDoor.Farfli.125 creates a Global\\vssafuyuhdw332kjgtts1 event and receives the addresses of the API functions it needs. To do so, it searches for the signature of two consecutive DWORD 0x8776633 and 0x18776655, starting from the trojan module base. This signature is located at the beginning of the last section of the module itself. With that, the section is nameless and contains various service strings, including the APU functions names, as well as a compressed trojan configuration.
The section contains three blocks of compressed data. The first block has the strings, the second block has the trojan configuration, and the third block remains empty. Herewith, the second and third blocks are located at the end of the section:
After the decompression, the second block represents a list of numbered strings listed below:
PS_10001=ole32.dll
PS_10002=CoCreateGuid
PS_10003=Shlwapi.dll
PS_10004=SHDeleteKeyA
PS_10005=wininet.dll
PS_10006=InternetOpenA
PS_10007=InternetOpenUrlA
PS_10008=InternetCloseHandle
PS_10009=HttpQueryInfoA
PS_10010=InternetReadFile
PS_10011=IMM32.dll
PS_10012=ImmReleaseContext
PS_10013=ImmGetCompositionStringW
PS_10014=ImmGetCompositionStringA
PS_10015=ImmGetContext
PS_10016=ADVAPI32.dll
PS_10017=GetUserNameW
PS_10018=RegCloseKey
PS_10019=RegOpenKeyExA
PS_10020=RegCreateKeyExA
PS_10021=RegSetValueExA
PS_10022=RegDeleteValueA
PS_10023=AdjustTokenPrivileges
PS_10024=LookupPrivilegeValueA
PS_10025=OpenProcessToken
PS_10026=StartServiceA
PS_10027=CloseServiceHandle
PS_10028=OpenServiceA
PS_10029=OpenSCManagerA
PS_10030=CreateServiceA
PS_10031=DeleteService
PS_10032=RegisterServiceCtrlHandlerA
PS_10033=SetServiceStatus
PS_10034=Shell32.dll
PS_10035=ShellExecuteExW
PS_10036=ShellExecuteA
PS_10037=User32.dll
PS_10038=PostThreadMessageA
PS_10039=wsprintfW
PS_10040=CharLowerA
PS_10041=GetMessageA
PS_10042=PostMessageA
PS_10043=CallNextHookEx
PS_10044=GetForegroundWindow
PS_10045=GetWindowTextA
PS_10046=GetWindowThreadProcessId
PS_10047=GetActiveWindow
PS_10048=UnhookWindowsHookEx
PS_10049=SetWindowsHookExW
PS_10050=SetThreadDesktop
PS_10051=OpenDesktopA
PS_10052=GetThreadDesktop
PS_10053=Kernel32.dll
PS_10054=GetModuleHandleA
PS_10055=DeviceIoControl
PS_10056=CreateMutexA
PS_10057=OpenMutexA
PS_10058=ReleaseMutex
PS_10059=CreateEventA
PS_10060=OpenEventA
PS_10061=SetEvent
PS_10062=WaitForSingleObject
PS_10063=GetLocalTime
PS_10064=GetTickCount
PS_10065=lstrcpyW
PS_10066=lstrcatW
PS_10067=lstrlenW
PS_10068=lstrcmpW
PS_10069=CreateThread
PS_10070=GetSystemDirectoryA
PS_10071=GetCurrentProcess
PS_10072=OpenProcess
PS_10073=MultiByteToWideChar
PS_10074=WideCharToMultiByte
PS_10075=Sleep
PS_10076=CreateFileA
PS_10077=DeleteFileA
PS_10078=WriteFile
PS_10079=ReadFile
PS_10080=CopyFileA
PS_10081=SetFilePointer
PS_10082=CloseHandle
PS_10083=GetModuleFileNameA
PS_10084=GetVersionExA
PS_10085=GetVersion
PS_10086=GetCurrentThreadId
PS_10087=GetFileSize
PS_10088=GetTempPathA
PS_10089=Psapi.dll
PS_10090=GetModuleFileNameExA
PS_10091=EnumProcesses
PS_10092=strstr
PS_10093=strchr
PS_10094=strcat
PS_10095=atoi
PS_10096=srand
PS_10097=rand
PS_10098=time
PS_10099=strrchr
PS_10100=strlen
PS_10101=strcpy
PS_10102=strcmp
PS_10103=memset
PS_10104=MSVCRT.dll
PS_10105=sprintf
PS_10106=memcmp
PS_10107=memcpy
PS_10108=GetLogicalDriveStringsA
PS_10109=CreateDirectoryA
PS_10110=MoveFileA
PS_10111=GetVolumeInformationA
PS_10112=FindNextFileA
PS_10113=FindFirstFileA
PS_10114=FindClose
PS_10115=GetDriveTypeA
PS_10116=GetFileAttributesExA
PS_10117=GetLastError
PS_10118=SHFileOperationA
PS_10119=GetCurrentProcessId
PS_10120=OpenInputDesktop
PS_10121=CreateToolhelp32Snapshot
PS_10122=Process32First
PS_10123=Process32Next
PS_10124=RegEnumValueA
PS_10125=EnumWindows
PS_10126=RegEnumKeyExA
PS_10127=ControlService
PS_10128=TerminateProcess
PS_10129=ShowWindow
PS_10130=BringWindowToTop
PS_10131=UpdateWindow
PS_10132=MessageBoxA
PS_10133=Winmm.dll
PS_10134=waveInOpen
PS_10135=waveInClose
PS_10136=waveInPrepareHeader
PS_10137=waveInUnprepareHeader
PS_10138=waveInAddBuffer
PS_10139=waveInStart
PS_10140=waveInStop
PS_10141=GetFileSizeEx
PS_10142=SetFilePointerEx
PS_10143=RegQueryValueExA
PS_10144=GetStdHandle
PS_10145=CreatePipe
PS_10146=SetStdHandle
PS_10147=DuplicateHandle
PS_10148=CreateProcessA
PS_10149=GlobalFree
PS_10150=GlobalAlloc
PS_10151=GlobalLock
PS_10152=ResetEvent
PS_10153=Gdiplus.dll
PS_10154=GdiplusStartup
PS_10155=Ole32.dll
PS_10156=CreateStreamOnHGlobal
PS_10157=CoInitializeEx
PS_10158=OpenWindowStationA
PS_10159=SetProcessWindowStation
PS_10160=ExitProcess
PS_10161=Wtsapi32.dll
PS_10162=WTSSendMessageA
PS_10163=WTSQueryUserToken
PS_10164=WTSGetActiveConsoleSessionId
PS_10165=DuplicateTokenEx
PS_10166=Userenv.dll
PS_10167=CreateEnvironmentBlock
PS_10168=DestroyEnvironmentBlock
PS_10169=ExitWindowsEx
PS_10170=CreateProcessAsUserA
PS_10171=ImpersonateSelf
PS_10172=OpenThreadToken
PS_10173=GetComputerNameA
PS_10174=GlobalMemoryStatusEx
PS_10175=GetSystemInfo
PS_10176=GetACP
PS_10177=GetOEMCP
PS_10178=Gdi32.dll
PS_10179=DeleteDC
PS_10180=CreateDCA
PS_10181=DeleteObject
PS_10182=BitBlt
PS_10183=CreateCompatibleDC
PS_10184=SelectObject
PS_10185=GetDeviceCaps
PS_10186=GetDIBits
PS_10187=CreateCompatibleBitmap
PS_10188=SetThreadAffinityMask
PS_10189=SetCursorPos
PS_10190=SendInput
PS_10191=ChangeServiceConfigA
PS_10192=EnumServicesStatusA
PS_10193=QueryServiceConfigA
PS_10194=GetCurrentThread
PS_10195=GetDiskFreeSpaceExA
PS_10196=GetEnvironmentVariableA
PS_10197=%08x.exe
PS_10198=ServiceMain
PS_10199=%s.dll
PS_10200=TWO
PS_10201=runas
PS_10202=%scom.exe
PS_10203=http://%s
PS_10204=%08x.txt
PS_10205=200
PS_10206=\svchost.exe -k
PS_10207=%SystemRoot%\System32
PS_10208=%ProgramFiles%\Common Files\Microsoft Shared
PS_10209=\Services\
PS_10210=ControlSet003
PS_10211=ControlSet002
PS_10212=ControlSet001
PS_10213=CurrentControlSet
PS_10214=SYSTEM\
PS_10215=%s%s%s%s\Parameters
PS_10216=%s%s%s%s
PS_10217=SeDebugPrivilege
PS_10218=ravmond.exe
PS_10219=rstray.exe
PS_10220=360tray.exe
PS_10221=ServiceDll
PS_10222=Start
PS_10223=Description
PS_10224=SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost
PS_10225=Windows Registry Editor Version 5.00
PS_10226=[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Messenger\Parameters]
PS_10227="ServiceDll"=hex(2):
PS_10228=%02x,00,
PS_10229=00,00
PS_10230=SOFTWARE\Microsoft\Windows\CurrentVersion\Run
PS_10231=rundll32.exe "%s",ServiceMain
PS_10232=ATI
PS_10233=ctr.dll
PS_10234=msgsvc.dll
PS_10235="%s",%s
PS_10236=rundll32.exe
PS_10237=%SystemRoot%\System32\
PS_10238=%ProgramFiles%\Common Files\Microsoft Shared\
PS_10239=%sreg.reg
PS_10240=%sreg.dll
PS_10241=SystemRoot
PS_10242=%s\System32\%s.dll
PS_10243=CommonProgramFiles
PS_10244=%s\Microsoft Shared\%s.dll
PS_10245=.upa
PS_10246=svchost.exe
PS_10247=-s "%s"
PS_10248=regedit.exe
PS_10249=%scpy.dll
PS_10250=CurrectUser:
PS_10251=Password:
PS_10252=[%04d-%02d-%02d %02d:%02d:%02d]
PS_10253=%s %s %s
PS_10254=***System Account And Password[%04d-%02d-%02d %02d:%02d:%02d]***
PS_10255=.txt
PS_10256=Default
PS_10257=Winlogon
PS_10258=%SystemRoot%\System32\msgsvc.dll
PS_10259=HARDWARE\DESCRIPTION\System\CentralProcessor\0
PS_10260=~MHz
PS_10261=SYSTEM\ControlSet001\Services\%s
PS_10262=rundll32.exe "%s",%s ServerAddr=%s;ServerPort=%d;Hwnd=%d;Cmd=%d;DdnsUrl=%s;
PS_10263=ServerAddr
PS_10264=ServerPort
PS_10265=Hwnd
PS_10266=Cmd
PS_10267=DdnsUrl
PS_10268=Default IME
PS_10269=iexplore.exe
PS_10270=SeShutdownPrivilege
PS_10271=WinSta0
PS_10272=Warning
PS_10273=Action
PS_10274=Error
PS_10275=DISPLAY
PS_10276=image/jpeg
PS_10277=NULL renderer
PS_10278=Grabber
PS_10279=FriendlyName
PS_10280=Cap
PS_10281=\%ssck.ini
PS_10282=\%skey.dll
PS_10283=\%skey.txt
PS_10284=%skey
PS_10285=%08x%s
PS_10286=%s\
PS_10287=%s\*.*
PS_10288=%s\%s
PS_10289=CMD.EXE
PS_10290=%s=
PS_10291=[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Messenger]
PS_10292="Start"=dword:00000002
PS_10293="Start"=dword:00000004
PS_10294=Messenger
PS_10309=\%s.dll
PS_10310=360safe.exe
PS_10311=\%sctr.dll
PS_10312=tmp.dll
PS_10313=ChangeServiceConfig2A
PS_10314=QueryServiceConfig2A
PS_10315=ServiceName
The trojan keeps the unpacked block with the strings in its memory and extracts these strings whenever it needs them, according to their specific numbers.
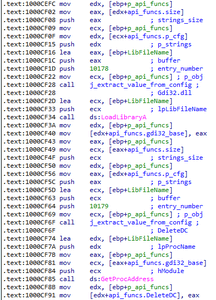
BackDoor.Farfli.125 consecutively loads all the required libraries, receives the addresses of necessary functions, and saves them inside the global structure through which it will call them. The code fragment, executing this routine, is shown on the next image:
After the necessary APIs are loaded, it finds the structure of the last section and unpacks the second block, which contains the configuration of the backdoor. This configuration contains the C&C address (www[.]pneword.net) and various parameters. The structure of the BackDoor.Farfli.125 configuration is as follows:
struct config
{
DWORD dword_0;
DWORD dword_1;
DWORD copy_to_temp;
DWORD port;
DWORD timeout;
DWORD delete_files;
DWORD start_keylogger;
DWORD cfg_dword;
DWORD dword_2;
DWORD dword_3;
BYTE srv_addr[256];
BYTE url[256];
BYTE unk_str[64];
BYTE gap_0[24];
BYTE name[312];
BYTE str_version32];
BYTE str_group[32];
BYTE password[32];
DWORD service;
DWORD dword_4;
GUID created_GUID;
BYTE gap_1[260];
};Next, BackDoor.Farfli.125 verifies the config.copy_to_temp flag. If its value is not 0, the trojan copies the .exe file from which it is running into the %TEMP% directory as a file with the <config.name>com.exe name pattern and launches it through the ShellExecuteA function. In the analyzed sample, the kfwktt is used for config.name in the file name. BackDoor.Farfli.125 uses the current executable module name as an argument for the command line.
After that, the trojan verifies the config.delete_files flag. If its value is not 0, the backdoor tries to read the %TEMP%\install00.tmp file and deletes the file whose name is stored in install00.tmp. Next, it deletes the install00.tmp, thumbs.db, rapi.dll and rapiexe.exe files.
BackDoor.Farfli.125 creates a C&C server connection object, initializes the Windows Sockets API, but does not establish the connection itself. Next, using the SetProcessWindowStation function, the trojan associates itself with WinSta0 and binds the thread to the Default desktop though the SetThreadDesktop function.
If the backdoor finds a config.start_keylogger flag, it initializes a keylogger. Upon its initialization, the mutex is created. Its name consists of two combined names of the module without a file extension:
<module_name><module_name>
Next, an event with the <module_name> name is created. The name for the log file is formed as follows:
%TEMP%\
To intercept the keystrokes, the window KBDLoger with the KBDLoger class name is created. With that, the interception is performed, using the RegisterRawInputDevices and GetRawInputData functions. The keylogger log file entries are encrypted with the XOR operation and the 0x62 byte.
BackDoor.Farfli.125 tries to read the <config.name>sck.ini file, which is supposed to contain the configuration for the trojan to operate as a SOCKS proxy server. This configuration contains the port number to which the proxy server binding is performed, as well as the name and the password for the authentication. The backdoor supports the SOCKS4 and SOCKS5 modes with capabilities to authenticate using the name and password and is able to resolve the domain names.
The operation in the SOCKS proxy server mode is performed in a separate thread. If the configuration file is missing, the trojan skips the proxy server creation stage.
C&C communication
The name of the С&C server is stored in config.srv_addr as a string. Moreover, config.url can store a URL, which the trojan uses to request a new address through the WinHTTP API. In this case, the response comes as a C&C server address string, which can also contain the port number, followed by :. The received address is saved in the %TEMP%\<threadid>.txt file, where <threadid> is the identificator of the current thread in the %08x format. Subsequently, the trojan reads the C&C server address from this file and applies it to its configuration.
BackDoor.Farfli.125 establishes a keep-alive connection through the TCP socket and generates the encryption key, using the XOR operation with one byte. Next, it extracts the config.password string from the configuration and forms a key in the size of 1 byte from it, using the following algorithm:
key = 0
i = 0
for x in password:
k = k ^ ((x << i) & 0xFF)
i += 1The config.password string in the analyzed sample is empty, so the data sent to the C&C server remains unencrypted.
BackDoor.Farfli.125 collects the following information about the system:
- OS version
- CPU frequency
- the number of processors
- the amount of RAM
- the name of the computer
- code pages for the ANSI and OEM
Next, based on the collected information, it prepares the structure as follows:
struct sysinfo
{
DWORD id;
DWORD dword_zero_0;
DWORD dword_zero_1;
DWORD dword_zero_2;
DWORD CPU_MHz;
DWORD dword_zero_3;
LARGE_INTEGER phys_mem;
DWORD ansi_CP;
DWORD oem_CP;
DWORD dword_0;
DWORD OS_version;
DWORD number_of_processors;
DWORD cfg_dword;
GUID created_GUID;
DWORD gap_0[5];
BYTE unk_str[128];
BYTE computer_name[16];
DWORD gap_1[28];
BYTE str_group[64];
BYTE str_version[32];
DWORD pad[9];
};id
When sending the first packet to the C&C server, the id field has a 0x1F40 value. When sending further packets, this field contains the command ID.
dword_0
The dword_0 field equals 1 if the id value corresponds to the 0x1F40; in other cases (i.e. if this is the first packet) it equals 0.
cfg_dword
The cfg_dword field equals the config.cfg_dword value.
OS_version
Depending on the version of the attacked operating system, the OS_version field can take the following values:
- 0 ― for Windows with the build number of 8XXXX and higher
- 1 ― for Windows 95
- 2 ― for Windows 2000
- 3 ― for Windows XP
- 4 ― for Windows Server 2003
- 5 ― for Windows Vista, Windows Server 2008
- 6 ― for Windows 7, Windows Server 2008 R2
- 7 ― for Windows 8, Windows Server 2012
- 8 ― for Windows 8.1 and higher
created_GUID
The created_GUID field is generated through the CoCreateGuid function each time the structure is sent to the C&C server. It is also saved in config.created_GUID.
unk_str
The unk_str string is copied from the config.unk_str. In the analyzed sample, this string is empty.
str_group
The str_group string is copied from config.str_group. In the analyzed sample, it has a value of General Group.
str_version
The str_version string is copied from the config.str_version. In the analyzed sample, it has a value of Customized Version.
After the structure is formed, it is encrypted with a one-byte XOR operation if there is a key and sent to the C&C server. If sending has failed, the thread goes to sleep for config.timeout milliseconds and tries to send the packet again. This routine is repeated until the structure is successfully sent.
If sending was successful, BackDoor.Farfli.125 receives a block, consisting of two DWORD in return. The first DWORD is the command ID, while the second DWORD is used in the reply to the command the trojan sends to the C&C server.
The operation with the commands
When responding to each command, the backdoor first verifies the packet with the sysinfo data, where the id field holds the ID of the received command, and the cfg_dword field represents the second DWORD received with this command.
There are two groups of commands BackDoor.Farfli.125 works with:
- the main commands
- the secondary commands; the backdoor starts to work with them upon receiving the commands with the 0x1F42, 0x1F43, 0x1F44, 0x1F4E and 0x1F54 IDs.
The main commands
| Command ID | Performed actions |
|---|---|
| 0x7535 | To obtain a SeShutdownPrivilege privilege and shut down the system with the SHTDN_REASON_MINOR_RECONFIG code. |
| 0x7534 | To obtain a SeShutdownPrivilege and reboot the system with the SHTDN_REASON_MINOR_RECONFIG code. |
| 0x7532 | To load a .DLL into the memory, call the ServiceMain function from it and delete the library. Due to possible error in the code, instead of the .DLL file, the trojan tries to load a text file with the keylogger log. If the .DLL was successfully loaded, the backdoor checks the value of the config.service. This value can be as follows:
The reg.reg file formed by the backdoor has the following contents: Where the ServiceDll name in it corresponds to the %SystemRoot%\System32\msgsvc.dll\ path. |
| 0x22B8 | To delete the keylogger log file. |
| 0x1F5A | To shut down the SOCKS proxy server and delete the configuration file. |
| 0x1F59 | To send the keylogger log file to the C&C server. The contents of the file are packed with the same algorithm as the data in the last section and sent in 3 stages:
|
| 0x1F58 | To receive a file name from the C&C server and then a buffer with the data. To open the specified file and write a received buffer into its end. |
| 0x1F57 | To record a sound through the microphone into the WAV file and send it as blocks to the C&C server. |
| 0x1F56 | To take a screenshot of the desktop and send it to the C&C server as a jpeg file. |
| 0x1F52 | To run a SOCKS proxy server. First, the trojan receives a configuration file, then binds a proxy server to a port specified in the configuration and starts to process the incoming connections. |
| 0x1F51 | To launch Internet Explorer with the command line arguments sent in the command. |
| 0x1F50 | To demonstrate MessageBox with the specified parameters. |
| 0x1F4B | To receive a file from the C&C server, save it in %TEMP%\<threadid>.<ext> and run it using the ShellExecute function. A file extension and nShowCmd parameter are also sent in the command. |
| 0x1F4A | To receive a URL from the C&C server from which a file will be downloaded. The trojan saves the file in %TEMP% and runs it. |
| 0x1F49 | To receive an executable module from the C&C server. In this module, the trojan searches for signatures similar to the one located in its last section. After this signature, it places the config.created_GUID value. Next, it saves a file in %TEMP%\<threadid>.exe and creates a process from it. After the process is successfully created, it performs the same actions as upon receiving the 0x7532 command. |
| 0x1F48 | To send a specified file to the C&C server. |
| 0x1F47 | A remote control using cmd.exe. The trojan redirects I/O to the pipes, receives the commands from the C&C server, sends them into the pipe set as hStdInput for cmd.exe, reads the results from the pipe set as hStdOutput. The results are compressed before being sent and the received commands are also compressed. |
| 0x1F41 | An RDP protocol imitation. The trojan takes desktop screenshots, sends them to the C&C server as .jpeg files and receives the input commands in response. |
The secondary commands
BackDoor.Farfli.125 sends the sysinfo structure to the C&C server with the 0x1F42 ID after it receives one of the following commands: 0x1F42, 0x1F43, 0x1F44, 0x1F4E, or 0x1F54. In response, the server sends a compressed block with the additional command’s ID and other data.
The result of the command execution is written into the %TEMP%\<threadid>.tmp temporary file first, where threadid is the ID of the current thread in the %08x format. Next, the file is read and its contents are packed and sent to the C&C server.
| Command ID | Performed actions |
|---|---|
| 0x1771 | To collect the information about the disk the path to which is specified in the command. The data is sent to the C&C server in the form of the structure shown below: |
| 0x1772 | To receive the information about properties of the file specified in the command. The result of the command’s execution is saved as the following structure: |
| 0x1773 | To receive the following information about a specified directory:
The command is executed recursively. The received information is saved as the following structure: |
| 0x1774 | To write a list of the files and subdirectories in the specified directory to the temporary file. The list represents a sequence of the file_info structures for each element. |
| 0x1775 | To delete files listed in the command. |
| 0x1776 | To create a directory. |
| 0x1777 | To move a file. The current and new file name are set as two consequent buffers of the size of 0x200 bytes. |
| 0x1778 | To list all available disks, forming a disk_info structure with the corresponding information for each of them. The collected data is sent to the C&C server in a response message. |
| 0x1779 | To open a specified file, calling the ShellExecuteA function with the nCmdShow parameter, which equals SW_SHOW. |
| 0x177A | To obtain a SE_DEBUG_PRIVILEGE privilege and terminate a process. The command contains the PID of the targeted process in a text format. |
| 0x177B | To list the contents of the registry key. For each element of the key the following structure is formed: |
| 0x177C | To delete a specified registry key. |
| 0x177E | To delete a parameter in the registry key. |
| 0x177F | To set a parameter value in the registry key. |
| 0x1781 | This command contains the list of paths to files and folders (one or more paths). If the path received in the command leads to the file, the trojan writes its name and size into the temporary file. If the path leads to the directory, the trojan recursively goes through it and for each file found in it, it writes its name and size into the temporary file. |
| 0x1782 | To create the list of active processes. For each process the following structure is formed: The collected information is sent to the C&C server. |
| 0x1783 | To create a list of running services of the SERVICE_WIN32 type. For each service the following structure is formed: |
| 0x1784 | To stop or launch a service. The command contains the buffer with the size of 0x200 with the service name, followed by a code. If the code is 1, the trojan needs to stop the service; if the code is 0, it needs to launch it. |
| 0x1785 | The command is responsible for the service configuration control. The trojan can change the type of the launch, the name, and the displayed name of the service. |
| 0x1787 | To delete a service. |
| 0x1788 | To search files, using the mask. The trojan saves the list of files with their properties in the temporary file. |
| 0x1789 | To list opened windows. For each window the trojan forms the following structure: |
| 0x178A | To close or show a window. The command contains a handle of the window, the code of the message, and the nCmdShow parameter. |