Compilation date:
- 03.04.2019 15:23:54
SHA1 hash:
- 3884263dfe67a3da0079fe40d6186950b853145c
Description
A backdoor trojan for 32-bit Microsoft Windows operating systems. It is written in C++. Its main functionality is to obtain unauthorized access to infected computers and perform malicious actions on behalf of attackers.
Operating routine
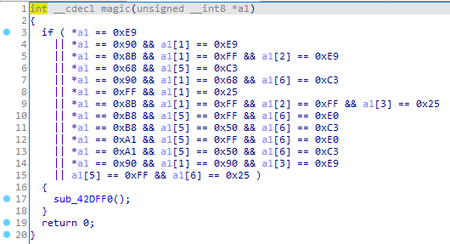
Upon launching, BackDoor.Siggen2.3238 initiates a series of preliminary checkups. First, it receives the addresses of the following exported functions:
- CreateDirectoryExW
- NtQueryDirectoryFile
- NtDeleteFile
- NtWriteFile
- NtReadFile
- NtCreateFile
- NtSetInformationFile
Next, it verifies the pointer to each function using the algorithm as follows:
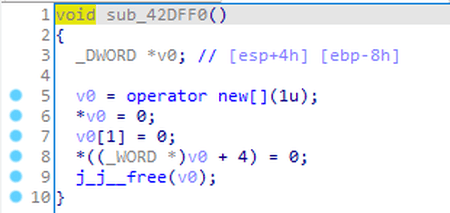
If the data at the pointer matches the one to be checked, the trojan allocates a memory region in the size of 1 byte, fills 10 bytes in this region with zeroes and tries to free it:
This operation is performed for each exported function. By doing so, the backdoor most likely checks for the active hooks in the functions and attempts to terminate the active process.
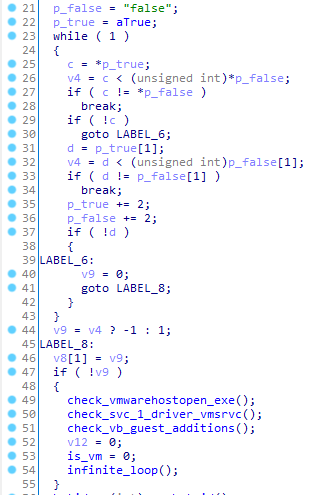
BackDoor.Siggen2.3238 then checks if the false and true strings hardcoded in its code are matching. If they match, the trojan checks for the VMWare and VirtualBox components, namely VMWare Guest Additions, Virtual Machine Additions and Virtualbox Guest Additions, are present in the system. After this verification is complete, its results are reset, and the trojan enters an endless loop where it doesn’t perform any other action.
The main functionality
BackDoor.Siggen2.3238 can connect to the C&C server using both HTTP and HTTPS protocols. The analyzed trojan sample uses the HTTPS protocol. When sending the requests to the server, the following User-Agent is used:
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; SE)
With that, all the requests are sent with the set of the parameters as follows:
%s;type=%s;length=%s;realdata=%send
where each %s string is correspondingly replaced by the strings shown below:
- the infected computer ID
- the type of the request to be sent
- the length of the data in the realdata field
- the data
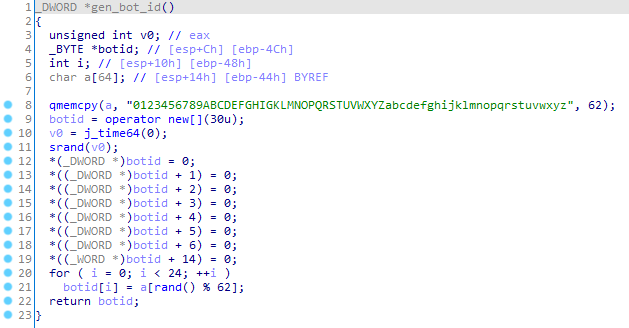
After the initial verification is complete, BackDoor.Siggen2.3238 generates its own ID using the following function:
Next, it collects the information about the infected system and forms the string shown below:
lan=%s;cmpname=%s;username=%s;version=%s;
where lan is the IP address of the infected computer, cmpname is the name of the computer, username is the user name, and version is a 0.0.4.03 string.
This information, paired with the sysinfo ID, is sent to the C&C server located at the https://31.214.157.14/log.txt. If BackDoor.Siggen2.3238 receives the HEART signal in response, the connection is considered successful, and the trojan proceeds to the main cycle of communication with the server.
To receive new commands, the backdoor sends the packet with the HEART command ID with the heart data. The server response that follows is parsed with the regular expression shown below:
type=([^&]+);first=([^&]+);second=([^&]+);third=([^&]+);
The type string in this response characterizes which command needs to be executed, while other strings contain the parameters for these commands.
BackDoor.Siggen2.3238 can receive the following commands:
| Command | Description |
|---|---|
| HEART | Heartbeat (Heartbeat (a beacon signal that keeps the C&C server and the backdoor connected). |
| OK | A server confirmation indicating the data sent by the trojan has been received successfully. |
| CMDINFO | To launch the cmd.exe with the input-output redirection into the pipes, through which the data is sent to the server and back. |
| PROCESSINFO | To collect information about the running processes. The information about each process is represented as proName=%1%;PID=%2%;proPath=%3%;Tport=%4%;Uport=%5%;descrip=%6%; |
| PROCESSTERMINATE | To kill the process with the specified PID. |
| LISTDRIVE | To collect information about disks. The information about each disk is represented as diskName=%s;driveType=%s;. |
| LISTFILE | To collect the listing of the specified directory. The information about each file or catalogue in it is represented as fileName=%1%;path=%2%;fileType=%3%;fileSize=%4%;access=%5%;create=%6%;. |
| DELETEFILE | To delete the specified file. |
| DOWNLOAD | To upload the specified file onto the server. |
| UPLOAD | To download the specified file from the server. |
| RUN | To launch the specified file. |