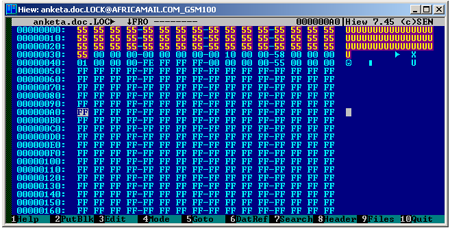
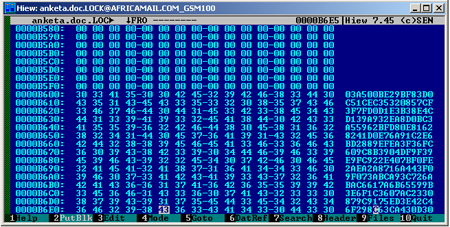
An encryption ransomware written in Delphi. First versions of this Trojan were discovered in April, 2011. Since then, new modifications of the program have been emerging with persistent regularity. The Trojan encrypts the user’s files using the RSA cipher, which makes decryption without the private key rather difficult. Moreover, due to the fact that the Trojan’s code contains a 32-bit variable, the malware adds its data to the beginning of the files larger than 4 GB. This results in these files being damaged and impossible to recover. The Trojan also adds several blocks of “garbage data” with a step of 0x400 bytes to the files.
The program saves the decryption information as a hexadecimal data block at the end of the files.
Usually, this Trojan does not modify file names. The message containing the ransom demand is displayed on the Windows Desktop. Cybercriminals can use the following email addresses: pomogiotkosit@yahoo.com, zog666@yahoo.com, harry.codder@yahoo.com, gruzinrussian@aol.com, evromaidan2014@aol.com, cryptolocker@aol.com, cryptfiles@aol.com.
Without the key, a partial decryption of the files affected by the actions of this malware is possible.