SHA1:
- 0913b7952eed88ba917c6965550de428c93b567b
- 091ea98e898c08488547fc7f02997e9913f79665
- 0bd12defaabe19429e76076c04efd5298dfe5a7b
- 0d09559555f5b4692d713a79cea6ad42d7b8e9bb
A Trojan for Android mobile devices. Embedded into different informational and entertaining applications published on Google Play. Android.Click.95 launches a browser to open a fraudulent website, where cybercriminals intimidate the users by falsely claiming that different malfunctions and vulnerabilities exist in the user’s mobile device and offer to install software to eliminate such “problems”.
Once Android.Click.95 is launched, it creates an AlarmManage timer with the following parameters:
- this.delayTimeFirst = 21600000—time in milliseconds, the interval between starting of malicious activity and the first launch of the Trojan.
- this.delayTime = 120000—time in milliseconds, the interval between the automatic visits to the fraudulent website.
Once the countdown in the first timer elapses, the malicious program checks whether some application specified in the Android.Click.95 settings is installed on the device.
Utils.checkApp(mContext, mContext.getPackageManager(), this.packName)If the Trojan does not find the application, it opens the fraudulent website, using the following parameters:
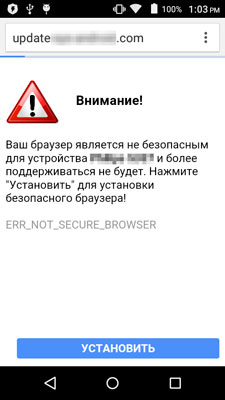
"http://update-***********.com/upd.php?text=notfound&model=" + Build.MODELA page notifying the user about a supposed problem will be downloaded from this link. For example, if Android.Click.95 has checked whether a specific web browser is installed on the device, the user will see a message that the current web browser is insecure. At that, the user is offered to click the “Install” button.
If the application is found, Android.Click.95 uses the following parameters to open the fraudulent website:
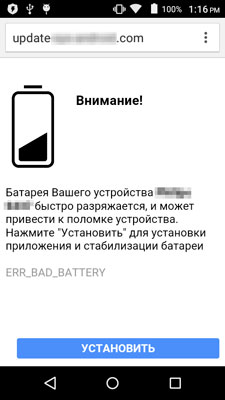
"http://update-***********.com/upd.php?text=found&model=" + Build.MODELIn this case a similar page is shown in the browser. This page contains an intimidating warning, without mentioning the monitored program. For example, a message about a battery malfunction can be displayed.
If the user agrees to install the cybercriminals’ program, the user is redirected to the relevant Google Play section.
Android.Click.95 opens the fraudulent website every 2 minutes from the moment when it has started functioning, making it irritating to use the infected device. At that, the maximum number of visits of the fraudulent website is limited to 1000 times.