SHA1 hash:
- 451cfa10538bc572d9fd3d09758eb945ac1b9437 (7zr.exe)
Description
The detection name for Windows programs that threat actors have implanted with a malicious component. The actual payload in such trojanized versions may vary.
Operating routine
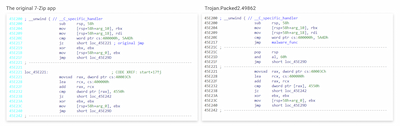
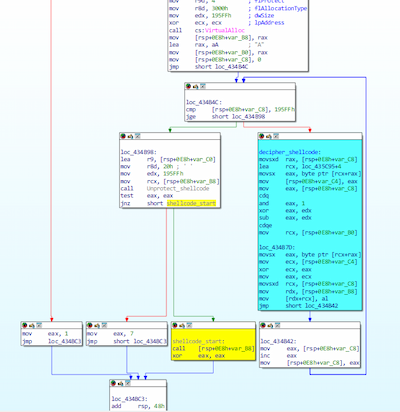
The original files of initially harmless programs are patched to run the implanted malicious payload. For this, a transfer command jmp is added to the start section of the apps. This transfer leads to a shellcode that decrypts the next malware stage.
A comparison of the original program’s code and the trojan version with the patch
Decrypting and running the embedded trojan shellcode:
Depending on which Trojan.Packed2.49862 variant is involved, the decrypted payload can be of the following types:
- a shellcode and the malicious executable that it runs;
- an encrypted shellcode created with an open-source instrument donut from which a malicious executable file is decrypted, extracted, and launched.
We have detected the following types of payloads being distributed via the modified programs:
BackDoor.ReverseProxy.1 (ReverseSocks5)
BackDoor.Shell.275 (AdaptixC2)
BackDoor.AdaptixC2.11 (AdaptixC2)
BackDoor.Havoc.16 (Havoc)
BackDoor.Meterpreter.227 (CobaltStrike)
Trojan.Siggen9.56514 (AsyncRAT)
Trojan.Clipper.808