SHA1 hash:
- e840c521ec436915da71eb9b0cfd56990f4e53e5 (pickmum1.exe)
Description
A trojan app written in the C# programming language and designed for computers running Microsoft Windows. Its body contains an encrypted multi-stage payload that allows attackers to download malicious programs from the C2 server.
Operating routine
When launched, Trojan.Inject5.57968 copies itself to %LOCALAPPDATA%\pickmum.exe and creates a task in the Windows scheduler to automatically run this file when the system boots.
Next, it decrypts a resource encrypted with the RC2 algorithm from its body. The resulting object is an executable file obfuscated with .NET Reactor (Trojan.PackedNET.3351). After that, Trojan.Inject5.57968 launches the aspnet_compiler.exe program from the Microsoft .NET Framework package and injects Trojan.PackedNET.3351 into the app’s process.
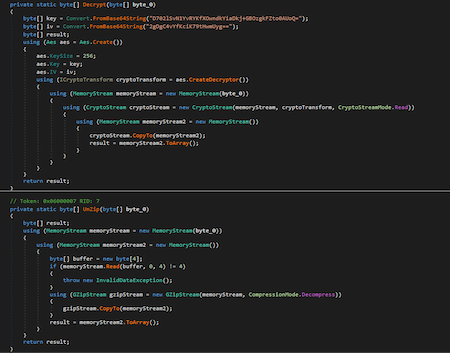
Trojan.PackedNET.3351 decrypts a data BLOB (a binary data array) encrypted with the AES algorithm from its body. The resulting file is a GZIP archive from which an executable file is extracted. This file implements backdoor functionality.
Trojan.PackedNET.3351’s code fragment that decrypts the binary data array (or BLOB)
The decrypted backdoor checks the environment for virtual machines and sandboxes. If they are not found, it connects to the C2 server at 64[.]95.11[.]202. To do so, it sends a string to the server whose MD5 hash is the encryption key for the backdoor’s subsequent operation. In response, the C2 server can send an encrypted payload that the backdoor will decrypt, unpack, and run.