SHA1:
- aeeaf0f9b21f8c9adedc5a72d7d4d1ce360d0150
Description
Malicious Android software module that implements clipper functionality. It is distributed as a pre-installed WhatsApp application, that is trojanized as part of a supply chain attack.
Operating routine
When the host application is launched, the LSPatch framework loads the module alongside it from the com.whatsHook.apk file. The com.whatsHook.HookMessage class allows changing the messenger behavior as follows:
-
On first run, it performs a POST request to <С2_name>/api/index/install, sending device information
{"type":"android","userid":"1","device":"ХХХХХХ","channel":"5003","deviceInfo":"{\"DeviceManufacturer\":\"Xiaomi\",\"DeviceProduct\":\"tissot\",\"DeviceBrand\":\"xiaomi\",\"DeviceModel\":\"Mi A1\",\"DeviceDevice\":\"tissot_sprout\",\"DeviceUser\":\"builder\",\"DeviceAndroidVersion\":\"9\",\"DeviceDefaultLanguage\":\"ru\"}","happName":"whatsapp"} -
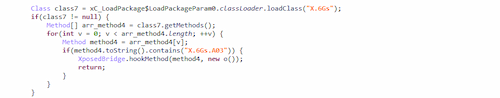
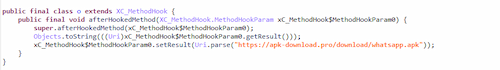
The module replaces a legitimate application update link with the one provided by the attackers. It does this by searching for the A03 method, which provides a link to download updates for the WhatsApp application.
Then it calls the о{} class that substitutes a legitimate update link for a URL provided by the scammers.
-
Intercepts outgoing and incoming WhatsApp messages. Searches for and spoofs TRX and ETH wallet addresses in WhatsApp messages. The spoofed addresses are either provided by the C2 server or the trojan uses values embedded in its code: TN7pfenJ1ePpjoPFaeu46pxjT9rhYDqW66 and 0x673dB7Ed16A13Aa137d39401a085892D5e1f0fCA. Sends all messages to the attacker's server.
-
Searches for.jpg, .png, and .jpeg files in the following directories and sends them to the attackers:
Environment.DIRECTORY_DCIM,
Environment.DIRECTORY_PICTURES,
Environment.DIRECTORY_ALARMS,
Environment.DIRECTORY_DOWNLOADS,
Environment.DIRECTORY_DOCUMENTS,
Environment.DIRECTORY_SCREENSHOTS
The clipper has been detected in devices whose names have been chosen to resemble model names of well-known brands. Some of the devices are manufactured under the SHOWJI brand name.
| SHOWJI S19 Pro | Note 30i | Camon 20 |
| SHOWJI Note 13 Pro | S23 Ultra | P70 Ultra |
| SHOWJI X100S Pro | S18 Pro | M14 Ultra |
| SHOWJI Reno12 Pro | 6 Pro | S24 Ultra |
MITRE matrix
| Stage | Technique |
|---|---|
| Initial access | Compromise Software Supply Chain (T1474.003) |
| Execution | Native API (T1575) |
| Persistence | Compromise Application Executable (T1577) |
| Collection | Clipboard Data (T1414) |
| Command and Control | Application Layer Protocol (T1437) Web Protocols (T1437.001) Encrypted Channel (T1521) |
| Exfiltration | Exfiltration Over C2 Channel (T1646) |
| Impact | Data Manipulation (T1641) |