-
SHA1 packed: 75df0fb24519d6f2b30f6df990d856e2ce905c73 (detected as Android.Click.770)
SHA1 unpacked: cf9b1bcb547886f1a00c7b40fd45bc838ce31175 -
SHA1 packed: 40627a814ed839689ac28f3a6077aa2cd72b8f8f (detected as Android.Click.773)
SHA1 unpacked: 941fec51d6fccd7476f524b0c75826bd40dd0ca6
An Android clicker, designed to subscribe users to expensive mobile services. It was first detected on Google Play, where it was spreading under the guise of harmless software, such as desktop wallpaper collections and camera apps. All known modifications of the trojan are packed using Jiagu.
When added to applications, Android.Click.322.origin embeds itself into well-known library packages, such as Facebook and Adjust SDK, to imitate them. See below the examples of the trojan’s activities and services, registered in manifest.xml after embedding into an app.
Imitated Facebook SDK:
<activity android:name="com.facebook.appevents.FacebookLogin">
</activity>
<activity android:name="com.facebook.appevents.FacebookPermission">
</activity>
<service android:name="com.facebook.appevents.FacebookEvent" android:permission="android.permission.BIND_NOTIFICATION_LISTENER_SERVICE">
<intent-filter>
<action android:name="android.service.notification.NotificationListenerService">
</action>
</intent-filter>
</service>
Imitated Adjust SDK:
<activity android:name="com.adjust.sdk.LoginActivity" />
<activity android:name="com.adjust.sdk.PermissionActivity" />
<service android:name="com.adjust.sdk.ActivityEvent" android:permission="android.permission.BIND_NOTIFICATION_LISTENER_SERVICE">
<intent-filter>
<action android:name="android.service.notification.NotificationListenerService" />
</intent-filter>
</service>
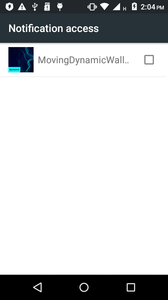
When launched, Android.Click.322.origin requests access to notifications:
After obtaining the permission, the trojan will be able to hide notifications about incoming text messages from the user and hook their contents.
Android.Click.322.origin transmits the following data about the infected device to the server at http://**.***.78.239:
- appId — the infected application version ID;
- carrier — the mobile carrier;
- condition — Internet connection type;
- country — the user’s country of residence, according to the settings;
- deviceId — the device identifier;
- imsi — SIM card ID;
- plmn — mobile network identifier;
- requestTime — time of request;
- url — the request type;
- version — the device model.
Then the trojan checks whether the victim’s SIM card belongs to one of the following countries:
- Austria
- Italy
- France
- Thailand
- Malaysia
- Germany
- Qatar
- Poland
- Greece
- Ireland
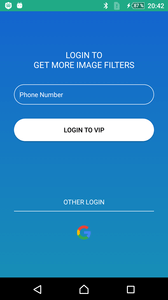
If there is a match, the trojan sends the mobile phone number, associated with the SIM card, to the server at http://**.***.78.239 using the standard TelephonyManager system class. The trojan also displays the FacebookLogin phishing activity to residents of certain listed countries, where it offers to enter a phone number or log into a Google account:
In the first case, the malware receives and sends the number entered by the victim. In the second case, it is taken from com.google.android.gms.auth.api.credentials.Credential after authorization.
If the SIM card does not belong to the target countries, the trojan does not take any action.
After sending the number, Android.Click.322.origin requests commands from the server at http://***.***.8.243:8998. The response contains a link to the website the trojan needs to open, as well as a specific JavaScript file.
Having received the task, the trojan creates an invisible View element with an invisible WebView. Then it uses the WebView to load the specified website and reports the success to the server at http://**.***.78.239. After loading the website, Android.Click.322.origin loads the previously obtained script in the WebView.
This script works via JavascriptInterface and can perform the following actions:
- getop() — obtain the data on the mobile carrier of the user;
- test(String str) — display a Toast with a certain text;
- upload(String param1, String param2) — transmit certain information to the server at http://**.***.78.239;
- finish() — remove the View containing WebView, unregister the BroadcastReceiver that receives the SMS data from notifications; send a new Intent to restart the process of receiving a command from the server.
Simultaneously with creating an invisible WebView, the malware initializes a BroadcastReceiver that tracks the Intents of the FacebookEvent Trojan service. This service controls the default text message application. Each time there is an incoming message, the service hides the corresponding system notification and creates an Intent with the contents of this message. The trojan BroadcastReceiver receives this Intent and sends the hooked text message to the server at http://**.***.78.239. Thus, the trojan bypasses the system restrictions and gets access to text messages without the standard permissions.
Android.Click.322.origin independently clicks the appropriate elements on downloadable websites, hides text messages with confirmation codes, and subscribes users to premium services.