Virus library
An analysis of the technologies used by cybercriminals allows us to draw conclusions about the virus industry’s possible vectors of development and more effectively confront future threats. You, too, can learn what actions various malicious programs take in infected systems and how to withstand them.
Adware.OpenCandy.243 in virus library:
A family of applications that serve the purpose of installing other software on the system. These programs are used by developers of free applications to generate income.
Main features of Adware.Opencandy are implemented in OCSetupHlp.dll that developers incorporate into their programs to make money. Once such a program is launched, the library is saved to a temporary folder, and, if there is an established Internet connection, a configuration file is downloaded from the command and control server. The configuration file script language has a rich syntax, which enables the malicious program to scan the computer for anti-virus software.
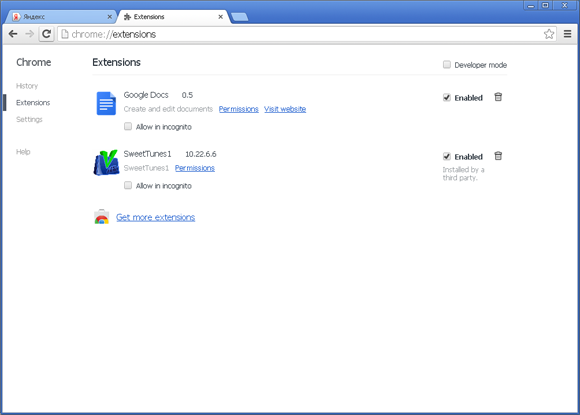
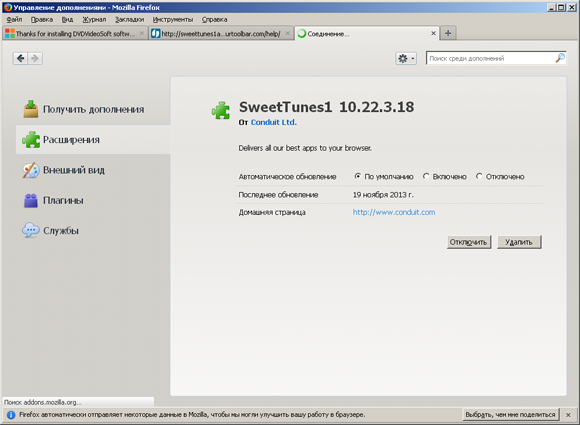
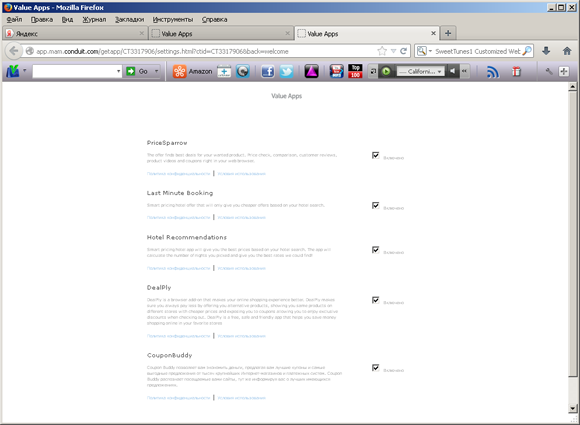
Once the configuration file is downloaded, various adware programs are uploaded to the computer. They contain a list of programs that the user will be prompted to install.
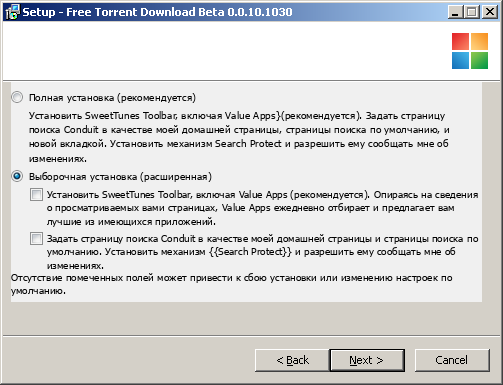
If the user agrees to install these components, the dlm.exe utility will be downloaded from the remote server. This program runs silently in the system background and is designed to install other software on the computer. By means of Adware.Opencandy, different browser bars and extensions, tools designed to replace browser start pages, and other adware applications (including “search helpers”, advertising modules, utilities for registry optimization, programs for “speeding up Internet connection”, and even malware belonging to the Trojan.Crossrider family) can be installed on the compromised machine.
It should be noted that software developers employing Adware.Opencandy to generate income cannot control the list of additional components and their number, which sets this family of unwanted programs apart from similar groups.
Vulnerabilities for Android
According to statistics, every fifth program for Android contains a vulnerability (or, in other words, a "loophole") that lets cybercriminals successfully introduce Trojans onto mobile devices and manipulate them into doing whatever actions they need them to.
Dr.Web Security Auditor for Android diagnoses and analyses a mobile device’s security and offers solutions to address security problems and vulnerabilities.