An installer of unwanted and dangerous programs for OS X. It is created using resources of an affiliate program called “macdownloadpro.com”. So far, more than 900 websites are known to take part in distribution of the installer.
The image of Adware.Mac.MacInst.1 has a rather remarkable structure; that is, it contains two hidden folders that cannot be viewed on the computer running with standard operating system settings if the user decides to browse the contents of the DMG file using Finder.
.app
.background
application.app
The directory with the application (in our case, application.app) contains a binary file that launches the installer from “.app\Downloader.app\Contents\MacOS”.
The “.app” folder contains two following subfolders:
.resources
Downloader.app
The “.resources” folder hosts the logo of the application and the encrypted configuration file. Decryption is performed by strings with the seed being reset to its initial value after every string.
The second subfolder contains the installer itself.
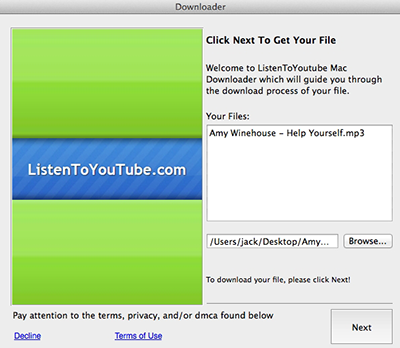
Once the installer is run, it demonstrates a dialogue window with the information on the file the user wanted to download.
After the “Next” button is clicked, the malware displays a partnership agreement informing the user that in addition to the file itself some other components will be installed. If the user clicks the hardly visible “Decline” link at the bottom of the window, only the initially chosen file will be downloaded. However, if the “Next” button is clicked, together with the file, the program detected by Dr.Web as Trojan.VIndinstaller.3 will be downloaded and run.
This application, in turn, installs malicious plugins for Safari, Firefox, and Chrome. These extensions are detected as Trojans belonging to the Trojan.Crossrider family. Adware.Mac.MacInst.1 copies all downloaded components into the “~/Library/Application Support/osxDownloader” folder.