SHA1: e2432fa6c53dfb62aeba242cd28fc4d51a70dbe3 (backdoor)
de5cc2779b9519bc3bbbda084f0b4cb858d2f890 (dropper)
A backdoor Trojan for Linux consisted of a dropper and a payload that performs main malicious functions.
The dropper is concocted using Lazarus, a free cross-platform IDE for the Free Pascal compiler. Once launched, it displays the following dialog prompting a user to enter their login and password:
Upon entering arbitrary values, except those that are hard coded in the Trojan’s body, such dialog boxes as "Initializing", "Connecting”, and "Signing in” appear on the screen subsequently. Then the next error message will be displayed: "Incorrect user ID or password. Please try again”. If a user enters specified credentials from the following list:
- j****/g***********
- m*****/f*********
- c****/j********
the Trojan’s response will be as follows: "An error occurred while attempting to login: invalid user token".
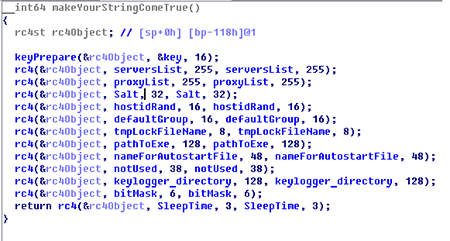
The second Trojan’s component—the backdoor itself—is saved to /tmp/.ltmp/ after the dropper is launched. Once the backdoor is running, it decrypts configuration lines encrypted using the RC4 algorithm. The decryption key is hard coded in the Trojan’s body. The configuration has the following structure:
serversList: a list of C&C servers that are used to establish connection to;
proxyList: a list of proxy servers through which connection may be established;
Salt: a line used to generate a password;
bitMask: a number that checks specified bits. If they are set to “1”, specified actions will be performed during initialization.
Values of bits:
| bit | Value |
|---|---|
| 0x1 | Copies itself in a location specified by a value of the pathToExe field in the configuration. |
| 0x2 | Processes the -m parameter: -m file removes a file or the file folder. |
| 0x4 | Unlocks its executable file for Read/Write. |
| 0x8 | Sets autorun through $HOME/.config/autostart. |
| 0x10 | Sets autorun through crontab. |
| 0x20 | Opens /tmp/$tmpLockFileName and write-protect it. |
| 0x40 | Launches a thread with a keylogger. |
| 0x80 | Executes the fork/chdir command. |
| 0x100 | Adds system proxies in a list of the necessary proxy servers. |
| 0x400 | Tries to connect via a proxy first when connecting to the server. |
| 0x800 | Connects via a proxy only. |
The .default.conf file is created in the folder with the executable file and has the following structure:
struct conf{
int32 magic; //0DE03C44h
char hostid[32];
char group[32];
}
Once the initialization procedure and the decryption of the configuration file are complete, the backdoor connects to one of the servers, sends the key to it and starts to execute commands. All of them, except a command with id=5, are encrypted.
The list of commands:
| id | Actions to perform |
|---|---|
| 5 | Gets the key for decryption of future commands from the server. It is the only message that comes decrypted and contains not only the key but also a buffer that is sent by the backdoor upon connection and is encrypted using the received key. |
| 7 | Closes all running files and resets encryption keys. In fact, it is a command to terminate the connection. |
| 8 | Removes itself from the autorun and turns itself off. |
| 9 | Sets the HostId field in the configuration file. |
| 10 | Sets the group field in the configuration file. |
| 11 | Makes HTTP request, saves the received file into the /tmp/ folder and executes it. |
| 12 | Runs a file, whose path and arguments are received from the server, which terminates the work of the backdoor. |
| 13 | Ends a connection and turns itself off. |
| 14 | Makes HTTP request and saves the received file into the /tmp/ folder. The server determines whether the file will be executed or not. |
| 17 | Sends a list of files and folders in a specified directory (without opening the folders). |
| 19 | Launches a thread that will check a specified folder for files matching a forwarded mask and sends them to the server until a command to terminate this thread is received. |
| 21 | Terminates a thread used for files downloading. |
| 22 | Opens a file, saves handle under the index number and sends its contents off to the server. |
| 23 | Writes to a file, whose handle is under the index number. |
| 25 | Copies a file. |
| 26 | Executes a system call for a new process creation and runs this process. |
| 27 | Renames a file. |
| 28 | Deletes a file. |
| 29 | Creates a folder. |
| 30 | Deletes a folder. |
| 31 | Creates a new folder or sends a list of files in a folder (recursively), depending on a value of the first 4 bytes. |
| 33 | Creates a zip archive with a specified folder. |
| 35 | Launches a thread that is used for executing the bash commands. |
| 36 | Sends a command to a thread that is used for executing the bash commands. |
| 37 | Terminates a thread that is used for executing the bash commands. |
| 39 | Sends information about a device and the .default.conf file. |
| 41 | Reads information from utmp. |
| 45 | Kills the process by its pid. |
| 46 | Receives a header of the current window. |
| 47 | Closes a specified window by sending it an event like ClientMessage : _NET_CLOSE_WINDOW. |
| 48 | Sends autorun files from the /usr/share/applications/ folder to the server. |
| 50 | Makes HTTP request and saves the received file into the /tmp/ folder. The server determines whether the file will be executed or not. |
| 52-53 | Generates the KeyPressed event. |
| 54 | Generates the ButtonRelease event. |
| 56 | Takes a screenshot and sends it off to the server. |
| 59 | Sends a list of files created by a keylogger if it is enabled. |
| 61 | Receives a size of a file created by a keylogger. |
| 62 | Deletes a file created by a keylogger. |
| 63 | Sends the contents of a file created by a keylogger to the server. |
| 67 | Receives information about open sockets from /proc and sends it to the server. |