- SHA1 hash: cfc35d28dad612e515a5f90a91fc7b33bcf7d7d6
Description
Android.Cynos.7.origin is the detection name for one of the versions of the Cynos software modules. They can be embedded into Android apps to monetize them. This modification’s main functionality is to collect information about users and their mobile devices and display ads.
Operating routine
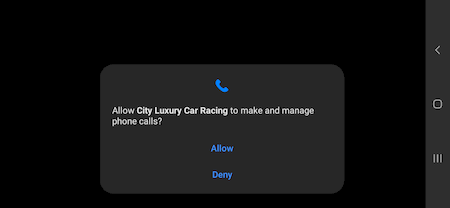
Upon launching the application containing the Android.Cynos.7.origin module, it asks the user for permission to make and manage phone calls. This permission allows the trojan to gain access to the information about the user’s mobile phone number:
Android.Cynos.7.origin randomly selects one of the C&C servers listed below and connects to it:
- hxxp://dns1[.]sdkbalance[.]com
- hxxp://dns2[.]sdkbalance[.]com
- hxxp://dns3[.]sdkbalance[.]com
In response, the module receives a server address to send the collected data to, and from which it can download the parameters required to display ads. If, for some reason, it is unable to receive the required address, the Android.Cynos.7.origin uses the following addresses hardcoded in the app’s code:
- hxxp://47[.]92.196.227—a server to transfer the collected data and log events to
- hxxp://39[.]100.129.237—a server to receive configuration required to display ads
The trojan collects and sends the following information to the server:
- Mobile operator’s MCC and MNC codes
- Device location based on GPS coordinates or the mobile network and Wi-Fi access point data (when the application has permission to access location)
- Mobile operator’s MCC and MNC codes
- GSM cell ID and GSM location area code (when the application has permission to access location)
- Device ID generated by the trojanized app (some trojan modifications use the device’s IMEI as its ID; some modifications also send the IMSI code, like SHA1: 8cce3b7c41a185919c4e7735176087b2e503741e)
- Device model
- The manufacturer
- An Android SDK version
- Screen resolution
- Internet connection type
- A CPU name
- App’s apk file md5 hash
- App’s version
- companyID—a parameter from the app’s metadata
- appID—a parameter from the app’s metadata
Before it sends the data, the trojan receives a public RSA key from the server. It uses a randomly generated key to encrypt the data with the AES algorithm. In turn, this key is encrypted with the public RSA key obtained earlier. Then, the encrypted key is sent to the server in the SecurityKey header of the request with the data.
Along with collecting data, this module’s other function is displaying ads inside the app that contains it. It uses different SDKs to display ads, depending on which app catalog is used to spread apps with Android.Cynos.7.origin. For example, if it's the AppGallery catalog, it uses com.Huawei.hms.ads. It uses com.Vivo.mobilead with the VIVO catalog, and com.Xiaomi.ad with the Mi store catalog. With the GameCenter catalog, it uses com.heytap.mobad.