Packer: absent
Compilation date: 01.12.2016 05:57:59
SHA1 hash:
- 4c871eae022c8088f6e8d46e17002cd0c0006650
Description
A backdoor written in C++ and designed to run on 64-bit Microsoft Windows operating systems. It is used for targeted attacks on information systems, collecting information about an infected device, loading functional malicious modules, coordinating their work, and providing communication with the C&C server. In the infected system, it exists as a DLL file and is loaded by the system service using the DLL Hijacking method. After injection, it functions in the computer's RAM.
Operating routine
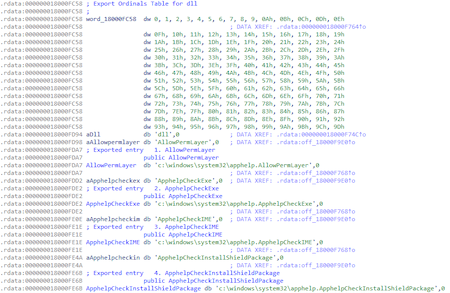
The backdoor is a malicious DLL file. The function names in its export table duplicate the exported functions of the apphelp.dll system library.
On the infected computer, the backdoor file was located in C:\Windows\System32\oci.dll catalog. The file’s original name from the export table is dll. It was loaded by the MSDTC system service using the DLL Hijacking method (Microsoft Distributed Transaction Coordinator Service).
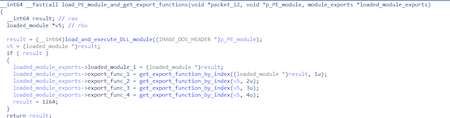
From a functional point of view, the sample is a loader for the main payload, which is stored in the .data section as a DLL, with some elements of the DOS and PE headers equal to zero.
The loader operation
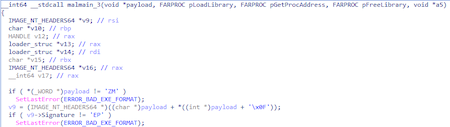
Loading is performed in a function designated as malmain_3 and called from the DLL entry point via two transitional functions.
First, the header signatures are checked. If they are not standard, the ERROR_BAD_EXE_FORMAT error value is set; however, this action does not affect the loader operation in any way.
The memory for the image is then allocated according to the IMAGE_NT_HEADERS64.OptionalHeader.SizeOfImage value, and the loader_struc auxiliary structure is formed.
struct loader_struc
{
IMAGE_NT_HEADERS64 *pPE_header;
LPVOID ImageBase;
HMODULE *p_imported_modules
QWORD number_of_imported_modules
HMODULE (__stdcall *pLoadLibrary)(LPCSTR lpLibFileName);
FARPROC (__stdcall *pGetProcAddress)(HMODULE hModule, LPCSTR lpProcName);
BOOL (__stdcall *pFreeLibrary)(HMODULE hLibModule);
QWORD unk;
};
This is followed by the standard process of loading the PE module into memory and calling the loaded module's entry point (DllMain) with the DLL_PROCESS_ATTACH argument, and after exiting it, calling it again with DLL_PROCESS_DETACH.
The main module operation
In the main module, the values of all signatures required for the correct file loading are equal to zero.
- IMAGE_DOS_HEADER.e_magic
- IMAGE_NT_HEADERS64.Signature
- IMAGE_NT_HEADERS64.FileHeader.Magic
In addition, TimeDateStamp and section names also have a null value. The remaining values are correct, thus after manually editing the necessary signatures, the file can be downloaded for analysis as a proper PE module.
The analysis of the main module is complicated, since atypical methods of calling functions are periodically used. The UT hash library is used for storing and processing structures. It allows one to convert standard C structures to hash tables by adding a single member of the ut_hash_handle type. All library functions, such as adding elements, search, delete, etc., are implemented as macros, which leads them to be forcibly inlined by the compiler in the code of the main (calling) function.
The mbedtls library is used to interact with the C&C server.
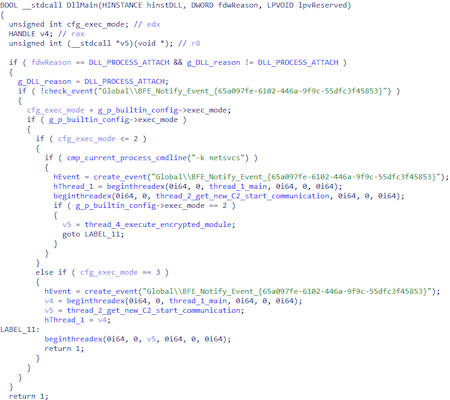
DllMain function
At the beginning of execution, the Global\\BFE_Notify_Event_{65a097fe-6102-446a-9f9c-55dfc3f45853}, event, execution mode (from the configuration), and the command line are checked, then the operating threads are started.
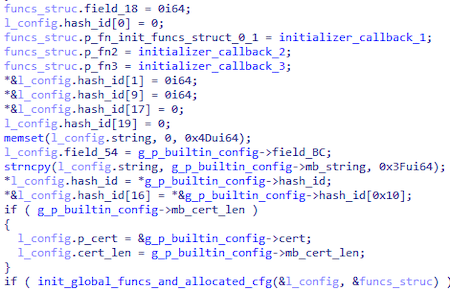
The module has an embedded configuration with the following structure:
struct cfg_c2_block
{
int type;
char field_4[20];
char addr[256];
}
struct cfg_proxy_data
{
DWORD dw;
char str[256];
char proxy_server[256];
char username[64];
char password[32];
char unk[128];
};
struct builtin_config
{
int exec_mode;
char url_C2_req[100];
char hash_id[20];
char string[64];
char field_BC;
cfg_c2_block srv_1;
cfg_c2_block srv_2;
cfg_c2_block srv_3;
cfg_c2_block srv_4;
cfg_proxy_data proxy_1;
cfg_proxy_data proxy_1;
cfg_proxy_data proxy_1;
cfg_proxy_data proxy_1;
int CA_cert_len;
char CA_cert[cert_len];
};
The hash field contains a value that can be an identifier. This value is used when communicating with the C&C server and can be represented as a b2e4936936c910319fb3d210bfa55b18765db9cc string, which is the same length as the SHA1 hashes.
The string field contains a single character string: 1.
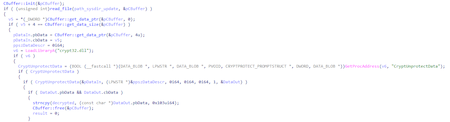
CA_cert is a certificate of the certificate authority in the DER format. It is used to establish a connection to the C&C server over the TLS 1.2 protocol.
Certificate information can be found in the notes to this description.
The DllMain function enables for the creation of multiple operating threads depending on a number of conditions.
- Main thread — thread_1_main
- New server request thread — thread_2_get_new_C2_start_communication
- Encrypted module execution thread — thread_4_execute_encrypted_module
For execution, the value of the builtin_config.exec_mode parameter must be non-zero.
- if the builtin_config.exec_mode value is 1 or 2, and the process command line contains the -k netsvcs substring, the main thread and the thread for getting the new C&C server address are started;
- If builtin_config.exec_mode is equal to 2, a thread that decrypts and runs the module stored in the system is started;
- If the value is 3, the main thread and the thread for getting the new C&C server address are started.
In the examined sample, the value of the exec_mode parameter is 3.
The main thread
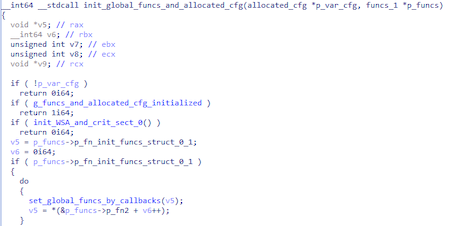
First, the backdoor checks the OS version then prepares a structure for initializing functions and a structure for storing a certain configuration fields. The procedure looks artificially complicated.
3 pointers to functions are inserted to the funcs_struc structure of the funcs_1 type that will be called in turn inside the init_global_funcs_and_allocated_cfg function.
In the set_global_funcs_by_callbacks function, each initializer function is called in turn.
The general order of structure forming is as follows:
- Two structures are passed to each function: the first contains pointers to some functions; the second is empty.
- Each function transfers function pointers from one structure to another.
- After calling the initializer function, the function pointers are moved from the local structure to the global array of structures at a certain index.
As a result, after all the unusual transformations, a certain number of global structures that are combined into a single array remain.
Ultimately, the function call can be represented as follows.
The use of complex transformations like copying local structures with functions and transferring them to global structures is probably intended to complicate the analysis of a malicious sample.
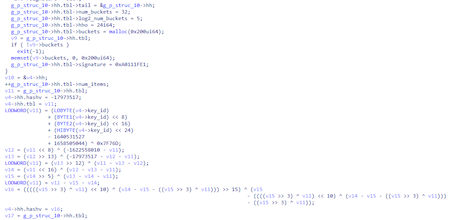
The backdoor then uses the UT hash library to generate a hash table of service structures responsible for storing the network connection context, connection parameters, etc.
Below is the fragment of the hash table generation code.
It is worth noting that the hash table contains a signature value that allows one to determine the library used: g_p_struc_10->hh.tbl->signature = 0xA0111FE1;.
The backdoor in question is characterized by the distribution of relevant fields and data across several structures created specifically for this purpose. This feature makes it difficult to create meaningful names for structures during analysis.
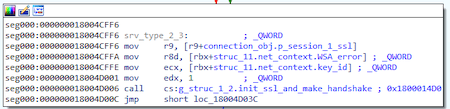
After the preparatory steps, the backdoor proceeds to initialize the connection to the C&C server.
Initializing the connection to the C&C server
It is noteworthy that the program code associated with the network connection contains its own error codes, in addition to the codes from the mbedtls library.
A list of error codes found in the sample.
enum ERROR_CODES
{
ERROR_CODE_1392 = 0x1392,
ERROR_BAD_ARGS = 0x5208,
ERROR_CODE_520B = 0x520B,
ERROR_CODE_520D = 0x520D,
ERROR_CODE_59D8 = 0x59D8,
ERROR_CODE_59DB = 0x59DB,
ERROR_CODE_59DC = 0x59DC,
ERROR_INVALID_ARGUMENT = 0x59DE,
ERROR_CODE_59DF = 0x59DF,
ERROR_CODE_61A8 = 0x61A8,
ERROR_BAD_ALLOCATION = 0x61A9,
ERROR_BAD_PACKET_SIGNATURE = 0x61AA,
ERROR_CODE_61AB = 0x61AB,
ERROR_CODE_61AC = 0x61AC,
ERROR_CODE_61AD = 0x61AD,
ERROR_CODE_61AF = 0x61AF,
ERROR_CODE_61B0 = 0x61B0,
ERROR_CODE_61B1 = 0x61B1,
ERROR_BUFFER_NOT_EMPTY = 0x61B2,
ERROR_CODE_6590 = 0x6590,
ERROR_CODE_6592 = 0x6592,
ERROR_BAD_ALLOC = 0x6593,
};
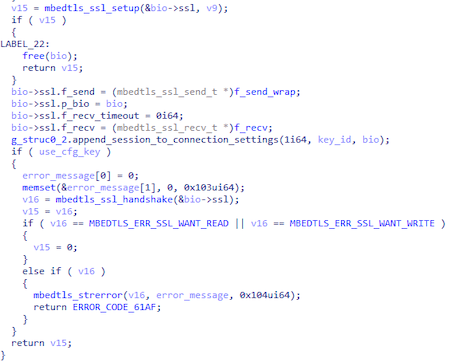
After a series of preparatory actions, the backdoor resolves the address of the C&C server stored in the configuration and retrieves the port. Addresses in the configuration are stored as strings: koran.junlper[.]com:80 and koran.junlper[.]com:443. Next, the program creates a TCP socket for the connection. After that, it creates a context for the secure connection and performs a TLS handshake.
After establishing secure connection, the backdoor expects a packet with a command from the C&C server. The program works with two packet formats:
- The packet received after processing the TLS protocol is a "transport" packet.
- The packet received after processing the transport packet is a "data" packet. It contains the command ID and additional data.
The transport packet header is represented by the following structure.
struct transport_packet_header
{
DWORD signature;
WORD compressed_len;
WORD uncompressed_len;
};
The data is placed after the header and packed by the LZ4 algorithm. The backdoor checks the value of the signature field. It must be equal to 0x573F0A68.
After unpacking, the resulting data packet has a header in the following format.
struct data_packet_header
{
WORD tag;
WORD id;
WORD unk_0;
BYTE update_data;
BYTE id_part;
DWORD unk_1;
DWORD unk_2;
DWORD len;
};
The tag and id fields together define the backdoor action, which means they denote the command ID.
These header structures are used in both directions of interaction.
The order of processing server commands:
- Client verification
- Sending the information about the infected system
- Processing commands by IDs
There is a variable that stores the state of the dialog in the structure responsible for communicating with the C&C server. Therefore, before directly executing commands, performing the first two steps is required, which can be considered as a second handshake.
A verification step
To perform the verification step, the values of the tag and id fields in the primary packet received from the C&C server must be equal to 1.
The verification process is as follows:
- The backdoor forms a buffer from an 8-byte array that follows the packet header and the hash_id field taken from the configuration. The result can be represented as the structure:
struct buff { BYTE packet_data[8]; BYTE hash_id[20]; } - The SHA1 hash of the data in the resulting buffer is calculated. The result is placed in the packet (after the header) and sent to the server.
Sending system information
The next packet received from the C&C server must have the tag value equal to 5 and id value equal to 3. The system data is formed as a sysinfo_packet_data structure.
struct session_info
{
DWORD id;
DWORD State;
DWORD ClientBuildNumber;
BYTE user_name[64];
BYTE client_IPv4[20];
BYTE WinStationName[32];
BYTE domain_name[64];
};
struct sysinfo_block_2
{
WORD field_0;
WORD field_2;
WORD field_4;
WORD system_def_lang_id;
WORD user_def_lang_id;
DWORD timezone_bias;
DWORD process_SessionID;
BYTE user_name[128];
BYTE domain_name[128];
DWORD number_of_sessions;
session_info sessions[number_of_sessions];
};
struct sysinfo_block_1
{
DWORD unk_0; //0
DWORD bot_id_created;
DWORD dw_const_0; //0x101
DWORD os_version;
WORD dw_const_2; //0x200
BYTE cpu_arch;
BYTE field_13;
DWORD main_interface_IP;
BYTE MAC_address[20];
BYTE bot_id[48];
WCHAR computer_name[128];
BYTE cfg_string[64];
WORD w_const; //2
WORD sessions_size;
};
struct sysinfo_packet_data
{
DWORD id;
sysinfo_block_1 block_1;
sysinfo_block_2 block_2;
};
The sysinfo_packet_data.id field contains a 0x19C0001 constant.
Thesysinfo_packet_data.block_1.bot_id value is extracted from the registry. The backdoor locates it in the instance parameter of the SOFTWARE\Clients\Mail\Hotmail\backup key, which, in turn, depending on the privileges, can be located in the HKLM or HKCU sections.
If the value is missing, a random GUID is generated using UuidCreate, then formatted as a XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXX string and saved. If the ID already existed, the sysinfo_packet_data.block_1.bot_id_created parameter is assigned the 1 value. If the ID was created, the parameter is assigned the 2 value.
The sysinfo_packet_data.block_1.cpu_arch parameter value:
- 1 — x86
- 2 — x64
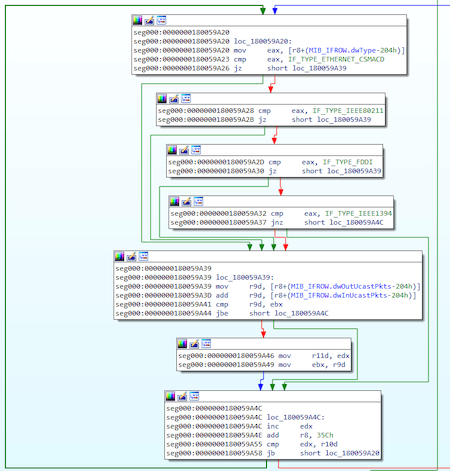
The process of determining the MAC address and IP address values by the backdoor is noteworthy. First, the program searches for the network interface through which the largest number of packets passed, then gets its MAC address and searches for the IP address of this interface.
The OS version is encoded with a value from 1 to 13 (0 if an error occurs, starting with 5.0 and then ascending the version.
The sysinfo_packet_data.block_1.cfg_string field contains the string value from the backdoor configuration, which is equal to the character 1.
Processing commands
After the verification step and sending the system information, BackDoor.Spyder.1 begins processing the main commands. Unlike most backdoors, whose commands are quite specific (pick up a file, create a process, etc.), in this instance, they are more of a service nature and represent instructions for storing and structuring the received data. In fact, all these service commands are aimed at loading new modules in PE format, storing them, and calling certain exported functions. It is worth noting that the modules and their information are stored in memory in the form of hash tables using UT-hash.
| tag | id | Description |
|---|---|---|
| 6 | 1 | Send the number of received modules to the server. |
| 2 | Save the parameters of the received module in memory. | |
| 3 | Save the body of the module in the memory. | |
| 4 | Load a previously saved module. The search is performed in the hash table by the ID obtained from the packet with the command. The module is loaded into memory, its entry point is called, then the addresses of the 4 exported functions are obtained, which are stored in the structure for further call. Call the exported function No.1. | |
| 5 | Call the exported function No.4 of one of the loaded modules, then unload it. | |
| 6 | Send in response a packet consisting only of the data_packet_header header, in which the unk_2 field is 0xFFFFFFFF. | |
| 7 | Call the exported function No.2 of one of the loaded modules. | |
| 8 | Call the exported function No.3 of one of the loaded modules. | |
| 5 | 2 | Send information about the current connection parameters to the server. |
| 4 | - | Presumably, the exported function No.1 can return a table of pointers to functions, and the program calls one of these functions at this command. |
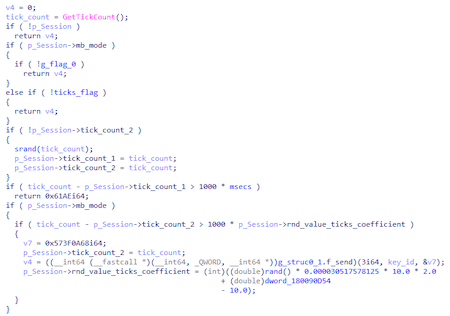
After processing each packet received from the server, the backdoor checks the difference between the two values of the GetTickCount result. If the value exceeds the specified reference value, it sends the 0x573F0A68 signature value to the server without any additional data and transformations.
New server request thread
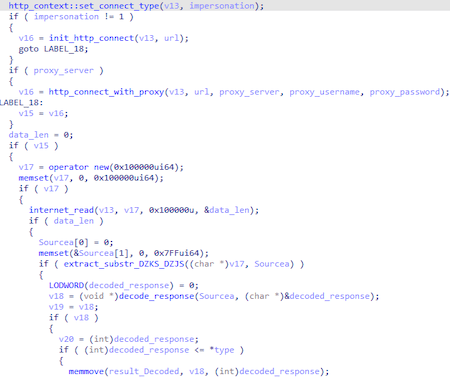
BackDoor.Spyder.1 can request the address of the new C&C server if the url_C2_req URL is provided in the configuration. To request this URL, the program can use both the system proxy and the HTTP proxy provided in the configuration. The request is made using the InternetOpenUrlA WinHTTP API.
The response must be a Base64-encoded string between two markers: DZKS and DZJS. It should be noted that a similar algorithm and markers were used in the PlugX family (BackDoor.PlugX.28 and BackDoor.PlugX.38).
The decoded string is decompressed using the RtlDecompressBuffer function, resulting in the address of the new C&C server and the port to connect to.
Encrypted module execution thread
If the exec_mode configuration parameter is set to 2 and the command line contains -k netsvcs, the backdoor creates a separate thread to execute the module stored in the file.
To do this, the backdoor searches for the C:\Windows\System32\1.update file at first. If such a file exists, the program reads it and decrypts it.
This file contains the path to an encrypted file containing a DLL module that the backdoor reads, decrypts, and loads.
Features of the x86 version
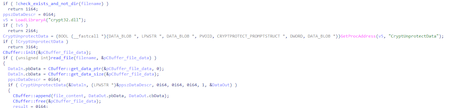
The version of the backdoor designed to run on 32-bit Microsoft Windows operating systems is detected by Dr.Web as a BackDoor.Spyder.3 (83e47dbe20882513dfd1453c4fcfd99d3bcecc3d). The main difference of this modification is the presence of debug messages.
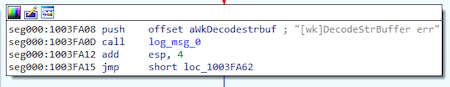
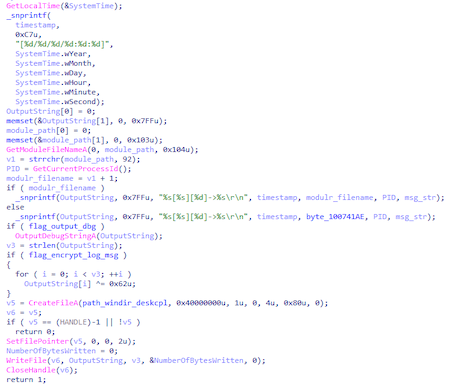
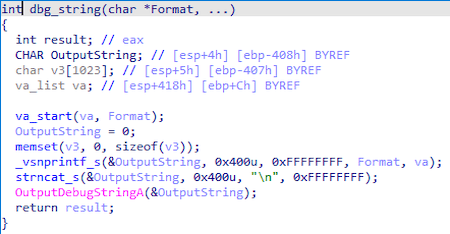
Messages are recorded on the log file located in the %WINDIR%\temp\deskcpl.ttf directory. Depending on the initialization parameters, they can be output using OutputDebufStringA or encrypted using a simple XOR operation with byte 0x62.
Messages related to communication with the C&C server and command processing are output using the OutputDebugStringA function. It is noteworthy that for such messages, the [Spyder] prefix is used.
Notes
Below is the information about the CA_cert certificate for establishing a connection with the C&C server:
SHA1 Fingerprint=BF:46:40:E4:AF:56:DB:E0:D0:86:6E:16:B0:3F:C7:23:77:26:14:31
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = SecureTrust CA, O = SecureTrust Corporation, C = US
Validity
Not Before: Jan 1 00:00:00 2011 GMT
Not After : Dec 31 23:59:59 2025 GMT
Subject: CN = SecureTrust CA, O = SecureTrust Corporation, C = US
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:bd:c3:26:8b:e1:37:7f:f0:fa:0a:0d:83:a7:dd:
22:31:14:83:08:d7:74:3b:31:08:84:ef:25:cf:2d:
44:fc:2d:54:77:0b:17:e2:70:4d:be:2f:c1:fc:ed:
d9:6b:9e:db:60:28:27:c4:1e:6d:15:3d:dd:b9:43:
64:37:58:b4:bd:48:85:fa:d1:d6:f7:5a:33:eb:ec:
b7:86:62:92:1f:89:d7:a4:bd:d3:1f:f3:18:9d:a4:
15:27:16:7b:26:9f:5c:53:87:bd:40:22:d2:5e:cd:
ab:d5:6f:1d:ac:c3:0d:f1:d9:d5:f5:6a:d3:16:76:
58:df:f7:0b:20:0d:ed:7b:97:ae:66:0a:e6:cc:9f:
73:50:fb:ce:16:a6:dc:45:d0:2f:70:3e:c8:c8:59:
4d:c4:62:ec:b0:e9:01:9c:57:92:e4:78:83:4f:a6:
ab:1b:94:45:ff:15:ed:dc:59:95:f3:71:22:9c:06:
38:bb:e6:0f:b3:ec:af:5b:bd:1a:2f:b1:7f:ce:c8:
4d:32:9f:8f:44:9b:ae:fc:e5:72:24:b4:3a:3b:f3:
d0:79:30:79:a2:0e:bd:55:e9:cd:c0:4d:7e:07:fc:
37:b5:7f:69:be:d6:e3:37:ce:9e:ff:d2:05:e4:3c:
59:7e:f0:d4:ab:01:e4:7b:07:f6:a4:f0:e3:c3:7e:
58:07:2d:e8:96:9c:ac:8b:e6:dc:49:6a:51:9a:b3:
b0:62:cf:3c:b4:4a:f9:89:ae:2c:73:17:01:43:63:
ec:e8:2b:7b:1c:3c:81:41:fa:db:93:45:3a:21:1f:
2a:3a:8f:30:d4:52:59:91:03:03:11:b8:18:ca:39:
4c:9a:e2:57:33:e6:bc:c5:4a:8e:76:79:50:fd:bd:
32:78:9c:79:58:4f:b9:d3:bb:05:eb:39:43:db:3e:
b5:2d:51:18:ed:ee:9d:31:3a:2e:6b:37:37:34:28:
4a:89:cb:65:b4:7d:bf:be:a1:67:cb:5c:71:9c:be:
c3:3b:f7:a7:df:37:4d:0f:c7:57:f5:5b:d2:db:54:
2c:91:5b:3b:7f:ec:1f:45:e4:7b:a5:0d:a1:c2:1f:
64:af:51:cd:32:3a:83:25:9c:90:ac:77:66:4d:12:
23:f5:5b:3c:90:b5:41:1b:54:55:a4:24:66:e6:e9:
65:46:95:ff:ef:67:f5:a6:80:f6:d5:e6:3f:2f:c2:
7b:25:d8:b3:b4:4d:f4:b8:7c:38:cc:de:3e:4f:43:
9a:ca:be:c1:66:95:2d:2c:16:a9:56:9b:68:5d:8c:
78:90:84:d4:86:51:10:f1:9b:14:23:43:bb:91:1e:
02:01:ee:11:63:c4:f2:81:7f:83:68:5e:86:bd:8a:
88:7c:2d
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
E0:63:19:89:FA:AD:19:5D:E3:B3:A5:E2:85:D2:2F:87:B1:55:76:1B
X509v3 Authority Key Identifier:
keyid:E0:63:19:89:FA:AD:19:5D:E3:B3:A5:E2:85:D2:2F:87:B1:55:76:1B
X509v3 Key Usage: critical
Digital Signature, Key Agreement, Certificate Sign, CRL Sign
Netscape Cert Type:
SSL Client, SSL Server, Object Signing, SSL CA, Object Signing CA
Signature Algorithm: sha256WithRSAEncryption
08:33:53:e4:be:95:0a:1b:d7:6e:44:6b:2d:42:2a:45:7f:8b:
89:fd:fb:d0:cf:5f:8f:83:77:5d:3b:2c:11:46:9f:44:3b:69:
f2:e2:e7:fe:4e:c9:43:5c:89:5f:e2:e2:5a:5e:4c:4d:39:ed:
ce:2d:63:d4:a1:93:ff:ff:3f:b0:77:86:e8:f1:5e:a3:4d:d3:
ba:eb:41:0f:85:0c:04:fb:6c:42:19:bc:2b:d1:db:c6:51:e3:
97:cd:5b:e5:d5:b4:1f:43:e7:7c:eb:86:08:16:86:0b:46:23:
9d:f4:e9:18:b6:ce:e5:f4:96:7b:ee:5f:f5:8d:ff:dd:65:29:
b9:12:94:f7:da:d3:c0:64:53:e6:2b:36:ec:6f:d3:26:3c:c2:
ab:ba:10:cd:d8:39:43:8b:21:fe:68:ab:48:25:34:07:a6:cc:
cc:b5:70:60:c4:ae:91:73:19:ff:9d:ff:82:ca:4a:9c:8e:70:
94:96:5f:7c:b3:e8:f7:e4:3e:cc:af:41:7e:24:47:fe:ad:d5:
a7:80:32:80:9c:7f:0c:00:3b:92:4c:ec:8e:ef:93:fb:8a:1f:
ff:be:f0:ab:33:c7:4b:2b:5d:fc:31:e6:bf:f4:1d:c0:e3:d0:
c5:94:a9:21:b1:8c:26:4b:c2:82:51:cf:1b:63:09:b1:ec:45:
31:49:ba:51:42:22:7a:41:90:2f:28:0e:40:76:91:3c:33:34:
84:66:b9:7e:0e:68:5a:37:38:01:b1:92:64:a5:a8:9c:34:84:
6a:c6:01:d0:30:f8:d5:52:0f:6e:3e:40:06:a2:b8:4c:b1:69:
4d:16:8f:d0:c4:72:b6:0e:09:57:6c:5e:cd:bc:ab:e3:ce:80:
ae:a7:6c:3d:3c:01:a5:a3:4f:4d:e0:52:36:12:cc:7a:e2:5e:
f3:d7:22:a7:6c:7c:60:d4:fd:f4:37:94:70:dd:4c:9b:00:cd:
7d:9d:42:f7:e7:b2:25:f6:63:06:1e:4d:dc:4b:ef:5c:45:5d:
a7:b9:b7:33:21:4e:91:40:ba:ca:ec:70:d0:a5:f7:0c:0a:ea:
97:11:fa:47:8b:dd:24:b0:c2:98:ff:94:4f:f6:c8:0f:e9:a5:
2d:bf:b6:7c:f4:45:f3:cb:5a:fd:a0:38:ce:ca:60:24:34:74:
77:ea:91:bc:dc:68:90:53:5f:0a:f4:40:13:69:68:2e:31:f9:
df:7d:07:05:53:42:8a:8b:e0:49:75:ee:04:94:9e:87:1a:25:
9e:82:16:87:a2:69:dd:eb:44:21:4c:98:1d:72:8b:46:74:5c:
33:24:5c:c2:ab:7b:1f:c4:d4:d5:9a:40:77:15:73:d3:53:62:
60:da:5d:7c:2a:9e:12:25
-----BEGIN CERTIFICATE-----
MIIFgTCCA2mgAwIBAgIBATANBgkqhkiG9w0BAQsFADBIMRcwFQYDVQQDEw5TZWN1
cmVUcnVzdCBDQTEgMB4GA1UEChMXU2VjdXJlVHJ1c3QgQ29ycG9yYXRpb24xCzAJ
BgNVBAYTAlVTMB4XDTExMDEwMTAwMDAwMFoXDTI1MTIzMTIzNTk1OVowSDEXMBUG
A1UEAxMOU2VjdXJlVHJ1c3QgQ0ExIDAeBgNVBAoTF1NlY3VyZVRydXN0IENvcnBv
cmF0aW9uMQswCQYDVQQGEwJVUzCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoC
ggIBAL3DJovhN3/w+goNg6fdIjEUgwjXdDsxCITvJc8tRPwtVHcLF+JwTb4vwfzt
2Wue22AoJ8QebRU93blDZDdYtL1IhfrR1vdaM+vst4Zikh+J16S90x/zGJ2kFScW
eyafXFOHvUAi0l7Nq9VvHazDDfHZ1fVq0xZ2WN/3CyAN7XuXrmYK5syfc1D7zham
3EXQL3A+yMhZTcRi7LDpAZxXkuR4g0+mqxuURf8V7dxZlfNxIpwGOLvmD7Psr1u9
Gi+xf87ITTKfj0SbrvzlciS0Ojvz0HkweaIOvVXpzcBNfgf8N7V/ab7W4zfOnv/S
BeQ8WX7w1KsB5HsH9qTw48N+WAct6JacrIvm3ElqUZqzsGLPPLRK+YmuLHMXAUNj
7Ogrexw8gUH625NFOiEfKjqPMNRSWZEDAxG4GMo5TJriVzPmvMVKjnZ5UP29Mnic
eVhPudO7Bes5Q9s+tS1RGO3unTE6Lms3NzQoSonLZbR9v76hZ8tccZy+wzv3p983
TQ/HV/Vb0ttULJFbO3/sH0Xke6UNocIfZK9RzTI6gyWckKx3Zk0SI/VbPJC1QRtU
VaQkZubpZUaV/+9n9aaA9tXmPy/CeyXYs7RN9Lh8OMzePk9Dmsq+wWaVLSwWqVab
aF2MeJCE1IZREPGbFCNDu5EeAgHuEWPE8oF/g2hehr2KiHwtAgMBAAGjdjB0MA8G
A1UdEwQIMAYBAf8CAQAwHQYDVR0OBBYEFOBjGYn6rRld47Ol4oXSL4exVXYbMB8G
A1UdIwQYMBaAFOBjGYn6rRld47Ol4oXSL4exVXYbMA4GA1UdDwEB/wQEAwIBjjAR
BglghkgBhvhCAQEEBAMCANUwDQYJKoZIhvcNAQELBQADggIBAAgzU+S+lQob125E
ay1CKkV/i4n9+9DPX4+Dd107LBFGn0Q7afLi5/5OyUNciV/i4lpeTE057c4tY9Sh
k///P7B3hujxXqNN07rrQQ+FDAT7bEIZvCvR28ZR45fNW+XVtB9D53zrhggWhgtG
I5306Ri2zuX0lnvuX/WN/91lKbkSlPfa08BkU+YrNuxv0yY8wqu6EM3YOUOLIf5o
q0glNAemzMy1cGDErpFzGf+d/4LKSpyOcJSWX3yz6PfkPsyvQX4kR/6t1aeAMoCc
fwwAO5JM7I7vk/uKH/++8Kszx0srXfwx5r/0HcDj0MWUqSGxjCZLwoJRzxtjCbHs
RTFJulFCInpBkC8oDkB2kTwzNIRmuX4OaFo3OAGxkmSlqJw0hGrGAdAw+NVSD24+
QAaiuEyxaU0Wj9DEcrYOCVdsXs28q+POgK6nbD08AaWjT03gUjYSzHriXvPXIqds
fGDU/fQ3lHDdTJsAzX2dQvfnsiX2YwYeTdxL71xFXae5tzMhTpFAusrscNCl9wwK
6pcR+keL3SSwwpj/lE/2yA/ppS2/tnz0RfPLWv2gOM7KYCQ0dHfqkbzcaJBTXwr0
QBNpaC4x+d99BwVTQoqL4El17gSUnocaJZ6CFoeiad3rRCFMmB1yi0Z0XDMkXMKr
ex/E1NWaQHcVc9NTYmDaXXwqnhIl
-----END CERTIFICATE-----
List of 32-bit modification debug messages:
[work]cmdline:%s
[work]dwDataLen=%d buf_temp=%d
[work]%s no exist
[work]get work err5
[aut]begin tid=%d.
[update_thread]begin tid=%d.
[update_thread]work=%s
[update_thread]get_work ret=%d
[update_thread]wait for work thread exit...
[update_thread]work thread exit ok
[update_thread]load work failed
[pt]proxy_thread begin tid=%d.
[]dwMajorVersion=%d dwMinorVersion=%d
[]rtlVer.dwMinorVersion=%d
[work]DllMain
[work] DLL
[work] VBR/SRV
[wk]RtlGetCurrentUserToken ok
[wk]ImpersonateLoggedOnUser ok
[wk]OpenURL %s Ret=%d
[wk]Err1
[wk]Err4
[wk]GetConfigStrFromURL err
[wk]DecodeStrBuffer err
[wk]DecodeLen err
[wk]RevertToSelf
[]IsProxyEnable Ret=%d
[aut]GetConfigStrFromURL PROXY_NO Ret=%d
[aut]GetConfigStrFromURL PROXY_USER Ret=%d
[aut]JmpAddClientConfig %s with address: %s.
[aut]GetRandom=%d
[aut]szWebURL Not Set
[aut]address_update_thread Exit.
[update_thread]get_work_path ret=%d
[pt]Using IE proxy setting.
[pt]IE proxy NOT setup.
[pt]SmpGetRegProxy Counts=%d
[pt]IE proxy type = %u NOT support, address: %s.
[pt]IE proxy type = %u, address: %s found.
[pt]Add proxy config %s, address=%s.
[work_thread]begin tid=%d
[wt]JmpAddClientConfig %s with address: %s.
[wt]JmpAddProxyConfig %s.
[wt]Proxy:%s
[wt]start Jumper error = %u.
[wt]Jumper start success!
[wt]JmpShutdown
[wt]JmpShutdown=%d
[wt]JmpTeardown=%d
[wt]tid=%d Exit
[Spyder] client module init error = %d.
[Spyder] register mod %d error = %u.
[spyder] alloc mem for ca cert failed.
[spyder] server address already exists in conf list.
[Spyder] alloc client error = %d.
[Spyder] ALLOC client uid = %u.
[Spyder] set ca for client id=%u error=%d
[Spyder] proxy setting exists, srv=%s
[spyder] use proxy [%s] to connect [%s] res = %u.
[Spyder] direct connect to %s error = %u.
[Spyder] connect to %s result = %u, protcol=%u.
[jmp] big packet: recv new big pkt while previous one not handled, old=%u, new=%u.
[jmp] packet size exceed limit = %#X, id=%u.
[jmp] failed to realloc packet buffer, error = %u, pkt id=%u.
[jmp] big packet recv completed, id=%u, size=%u, ext id=%u.
[Spyder] PAUSE ext = %u Before.
[Spyder] PAUSE ext = %u After.
[Spyder] UNINIT ext = %u Before.
[Spyder] UNINIT ext = %u After.
duplicate session id for ext type id = %u.
[Spyder] can't find recv item for type id = %u.
[Spyder] ext type id = %u recved = %u, new recv = %u, but total size = %u
[Spyder] ext type id = %u recv completed, total size = %u.
[Spyder] find ext with same type id = %u while updating, free old ext.
[Spyder] alloc mem for completed ext error = %u.
[Spyder] ext recv %s, free tem buffer, type id = %u.
[Spyder] ext type = %u already loaded, unlaod now for updating.
[Spyder] failed to unload ext from memory.
[Spyder] load ext id = %u into memory error.
[Spyder] MOD LOAD AT %p, size=%u.
[Spyder] alloc mem for loaded item failed, unload ext type id = %u.
[Spyder] inint module type = %u begin.
[Spyder] inint module type = %u end.
[Spyder] alloc mem for mod_pfn error = %u.
[Spyder] unlaod ext id = %u error.
[Spyder] unload_and_free_all_exts.
[Spyder] UNLOAD ext = %u BEFORE.
[Spyder] UNLOAD ext = %u AFTER.
[Spyder] FREE ext = %u AFTER.
[Spyder] free ext cache = %u .
[Spyder] free ext mem = %u .
[Spyder] link setup Result=%d, local = %#X:%u, remote = %#X:%u, uid=%u.
[Spyder] connected callback at %02u:%02u:%02u, id = %u.
[Spyder] Link disconnected at %02u:%02u:%02u, id = %u.
[Spyder] recv data size = %u invalid, from uid=%u.
[Spyder] receive challenge = %I64X.
[Spyder] failed to get host info.
[Spyder] send host info error = %u.
[jmp] LOGIN SUCCESS, link id = %u.
[jmp] internal data process error.
[jmp] unknown state = %u.
[jmp] core process data error, close link = %u.
[Spyder] ext summary size error = %u.
[Spyder] ext recv prepare failed.
[Spyder] EXTENSION recv BEGIN, type = %u.
[Spyder] dll payload recv error.
[Spyder] ext active begin.
[Spyder] ext active result = %s.
[Spyder] ext free cmd not handled.
[Spyder] unhandled ext sub cmd = %u.
[Spyder] call ext failed = %d, sub=%u.
[spyder] unhandled subcmd=%u in tunnel cmd.
[Spyder] unhandled main cmd = %u, sub cmd = %u.
[Spyder] Can't get link id for ext data delevery.
[Spyder] SEND_DATA via link id=%u error = %d.
[Spyder] client link disconnect id = %u.
[Spyder] client send data error = %#X, id = %u.
[Spyder] enum session error = %u.
[Spyder] get Host info error.
[Spyder] save sn value error = %u.
[Spyder] gszUniqueSN=%s
[Spyder] create guid error = %d.
[jmp] Get adapter info error = %u.
[jmp] adapters info buf size=%u, count=%u.
Alloc buf for adapter info error = %u.
get adapter info with buf error = %u.
[jmp] IP=%s not match preset mac address, desc=%s.
[jmp] master adapter FOUND! IP = [%s], desc=%s.
[jmp] master adapter has more than one ip: %s.