SHA1:
- db6d99702dd8bb19c2a7608094ab3b4e9535d266
- 9db691d2e302cbd6e7beba7f71e675911a17a6c7
A Trojan for Linux, including Air OS that is developed by Ubiquiti Networks and installed on its devices. It is implemented as bash scripts distributed in the archive tgz. Implements the following modifications in file /etc/passwd:
moth3r:$1$RpWdAhdc$cNgp9llO5jKApRaG8b4nK1:0:0:Administrator:/etc/persistent:/bin/sh
The contents of the archive:
download
infect
mfid
mfid.pub
mother
p
passlst
passwd
scan
sprd
p
Checks the system for the user account with login "moth3r". If there is no such account, the Trojan creates it. Checks if the Trojan is registered in the autorun, and if it is not registered—it specifies in file /etc/persistent/rc.poststart the unpacking of its own archive and launch of the “mother” script.
Deletes SSH keys and restarts the device.
download
Installs on the infected device curl, libcurl, libssl, libz, and allows downloading and running arbitrary files. In the body of the download file there is a link to website pastebin.com. If the file that is located through the link contains word "nomorelies”, and hash of the corresponding file fragment is equal to "d709745c628f6682ae506d54e4320a28”, then this file will be saved and executed.
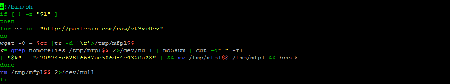
mother
Blocks access to the infected device through ports 80 and 443. Checks the system for a user with login "moth3r”, and if it is not available—it creates one.
Sets the following ssid to the wi-fi network: "mootherf u c k e r". Initiates scanning of subnets accessed by the device.
scan
Forms IP address in the cycle and launches the infect script, thus transferring the formed IP address as a parameter.
infect
Can take on 4 arguments:
- IP address of the infected device;
- String "dbss";
- SSH port;
- Protocol type ("http" or "https").
If SSH port is not specified, the script searches for the appropriate port by addressing ports 22 and 222. If the response contains string "dropbear”, this port is considered to be the required one.
If string "dbss” is indicated as an argument, and an SSH port is indicated or found, the script connects to the device via the SSH protocol using the key (MFID) and installs itself on this device.
If the protocol type is not indicated, the connection is executed via the http protocol, then—via the https protocol. Searches for the "airos" string in the reply.
If the Trojan successfully defines the protocol (or if protocol is indicated as an argument), the infection of devices is executed with the use of web interface vulnerability that allows downloading an arbitrary file through an arbitrary path without authorization.
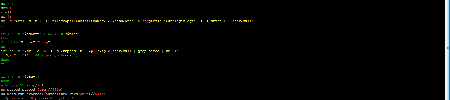
The Trojan overwrites files /etc/passwd and /etc/dropbear/authorized_keys, and replaces them with its own, after that it connects to the device via the SSH protocol using the key.
If the Trojan cannot define the protocol (or Air OS is not installed on the infected device), it can make an attempt to generate account details for the SSH connection using a special dictionary with the use of logins “root”, “admin”, “ubnt” and passwords stored in the “passlst” file.
passwd
Contains only one user—moth3r.
moth3r:$1$J1CHZtqy$n0XDmW4UCVAVYZqFzvoEC/:0:0:Administrator:/etc/persistent:/bin/sh
